Key Marketing AI Concepts (In Plain English!)
Dataiku
MAY 28, 2020
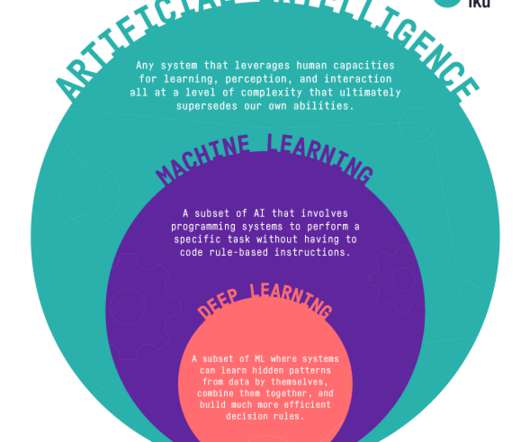
Today’s marketing teams have no shortage of business questions they want to solve, yet they run into all kinds of challenges when trying to make AI a reality. One of them is wanting to democratize the use of AI and data but unable to do so due to a lack of knowledge and transparency around how AI-based technology works.


































Let's personalize your content