Enabling Secure Access for the Federal Government – Meeting Comply to Connect Mandates
Government IT organizations must demonstrate and maintain compliance with a large and growing number of regulations and standards around network access control (NAC), ensuring that all connected devices to their environment are not vulnerable is a key requirement.
Comply to connect (C2C) simplifies this by enforcing that patches and hardened configurations are applied to devices before they connect and updated continually. Ivanti has been helping federal civilian, intelligence, and Department of Defense (DOD) agencies do exactly that – swiftly, seamlessly, and cost-effectively. Ivanti’s Pulse Secure solution provides holistic secure access for local and remote access based on user and device identity.
Comply to Connect demands that any endpoint is vetted against established security requirements before connecting to your agency’s environment. Some vendors enable Comply to Connect in an agentless mode. Agentless solutions allow you to inspect endpoints from a distance before permitting or disallowing the device from connecting to the network. However, for the agentless solution to work, the device must get Layer 3 access via an IP address. Therefore, you have given potentially non-compliant devices access to your network during the very process of vetting the device.
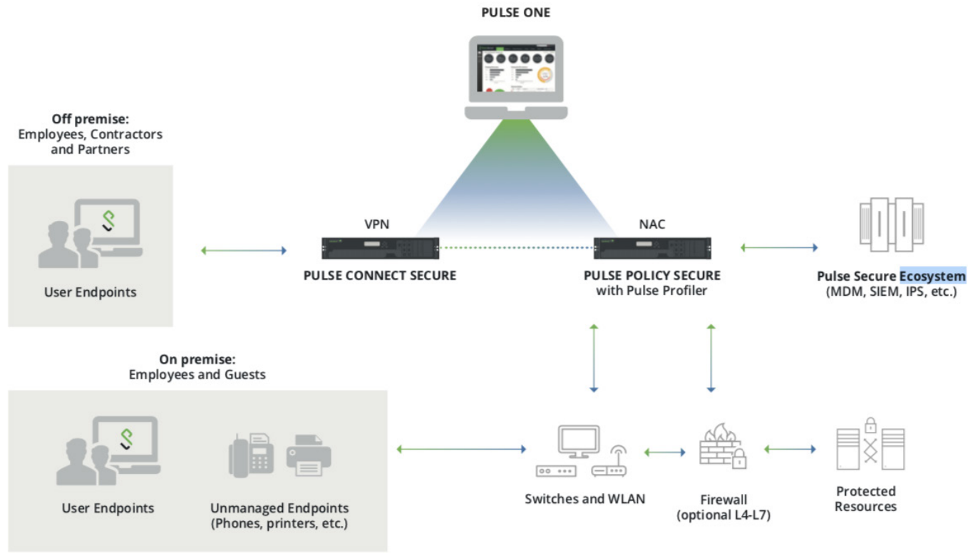
With a Pulse Secure agent, an IP address is never given. The device never gets a full connection to the network during the validation cycle. Comply to Connect validations are performed at Layer 2 without requiring that the device access the network.
Pulse Secure solution is most effective for the following reasons:
- An IP address is never given so the device never gets a full connection to the network during the validation cycle.
- The Pulse Secure agent is always on and performs continuous monitoring, so any changes are caught in real-time.
- The need for the potentially risky Windows Management Instrumentation (WMI) protocol being used is eliminated.
To learn more about why Ivanti recommends the implementation of a Pulse Secure agent for government agencies aligning with Comply to Connect directives visit Solution Brief - Secure Access for the Federal Government or visit Secure Access for the Federal Government webpage.
