Symantec Mobile Threat Defense: Speak the Language of Business with Your Security Policy
A mobile security policy based on compliance and risk tolerance can lower cyber fatigue, align mobile device risk with business goals
Cyber security professionals have it tough (to say the least).
To begin with, they work in an industry where the solution is often part of the problem. With every new threat and vulnerability come new security products. With every new security product come more tools to maintain and more telemetry to analyze. More data, more protections, more complexity…more worry. Symantec’s Senior VP for EMEA, Stuart Henderson, put it best when he wrote, “There’s a cruel irony to the fact that tools and systems designed to help protect the enterprise are increasing stress.”
At the same time, the purpose of a security leader’s role within an organization is also evolving. Today, security practitioners are expected to go beyond data protection and threat prevention and wear the hat of business enabler. Aligning with business goals is becoming an increasingly critical requirement of enterprise security teams; according to Gartner, by 2020 100% of large enterprises will be asked to report to their Board of Directors on cyber security risk at least annually (an increase from 40% in 2016). The problem is that security practitioners often get so caught up with catching up on every threat and how to respond, that they lose sight of the bigger business goals.
At Symantec, we believe one way to reduce cyber fatigue, while also helping security leaders be better business enablers, is to rethink how security policies are defined in enterprise security solutions.
At Symantec, we believe one way to reduce cyber fatigue, while also helping security leaders be better business enablers, is to rethink how security policies are defined in enterprise security solutions. Specifically, in mobile threat defense (MTD), we advocate for mobile security policies that focus on compliance and risk control, an approach that is more scalable and sustainable compared to focusing on specific threats.
The concept of a “mobile security compliance policy,” unique to our MTD solution, Symantec Endpoint Protection Mobile (SEP Mobile), simplifies how security administrators manage security threats and compliance across all mobile endpoints. The policy allows security leaders to set a mobile security risk tolerance that is in line with business objectives – without having to know what a “suspicious dylib” is or what “SafetyNet API” stands for.
Common Mobile Security Policy Approaches
MTD solutions allow organizations to set a policy to ensure both the security of employee mobile devices and the IT resources accessed through them. The policy generally includes procedures and rules governing threat protection actions, end-user communications, privacy controls, risk tolerance and other factors. Like IT security policies in general, a mobile security policy is unique to each organization, changing according to the information the enterprise values and how much risk it is willing to tolerate. We focus on the latter – risk tolerance – in this article.
In most MTD solutions, mobile security policies are threat-based. This means admins must set either a severity level or response action for each specific, known mobile threat. Think of it like an “if-then” scenario: if an app is found to be leaking sensitive data from a device (threat), then the MTD agent should terminate the app’s processes (action). This definition process continues until every threat in the system is covered. To give an idea of the scale of this task, in SEP Mobile today there are dozens of threat detections, each with multiple severity levels, and more detections are continuously added.
While the threat-based approach appears to allow a high level of granularity and control over how to respond to each specific threat, it has drawbacks that can make the work of security practitioners more burdensome:
- Difficulty in seeing the bigger picture: The need to focus on every single threat makes it more challenging to zoom out and look at the overall state of mobile security and how it aligns with the company’s risk tolerance.
- Level of expertise required: Similarly, admins are expected to be experts on every existing and new mobile threat. Not all threats are created equal in terms of the risk they pose to an organization. In order to assign a risk level or choose an effective response, security practitioners must dive deep into a threat. To give an example, in a previous article we explored what goes into the risk classification of content manipulation threats: deep analysis, granular pattern matching and recursive inspection that SEP Mobile’s research team conducts on an ongoing basis to effectively classify the severity of each threat. It is not practical to expect every organization’s security team to match this level of analysis.
- Continuous maintenance: Admins must define a risk level and/or action for every new mobile threat that emerges. This requires constant maintenance and updates to the security policy.
- Insufficient policy controls: When looking only at threats, admins may miss other risk factors which can also violate a company’s security policy, i.e. unapproved device hardware.
One Compliance Policy to Rule Them All
Rather than requiring admins to define their security policy threat by threat, SEP Mobile allows organizations to define a single mobile security compliance policy that encompasses all mobile device risk. In this policy, an organization can decide what level of risk it is willing to accept to meet its business goals. Then, SEP Mobile does the legwork, providing the severity of threats to mitigate risk according to the organization’s defined risk tolerance. We bake machine learning and artificial intelligence into this process, allowing for faster and more accurate risk classifications.
From the moment the compliance policy is set, admins do not have to update it as new threats surface. For example, we recently introduced a new high-risk indicator of compromise (IoC) in SEP Mobile, known as “open remote access.” This detection allows SEP Mobile to identify whether iOS devices can be remotely accessed via an open service port, which can be exploited by malicious actors. If an organization defines in its compliance policy that any devices with “high-risk indicators of compromise” should be considered non-compliant, then any device on which SEP Mobile detects a high-risk IoC – including the open remote access IoC, and any other existing or future IoCs – will fall into this category.
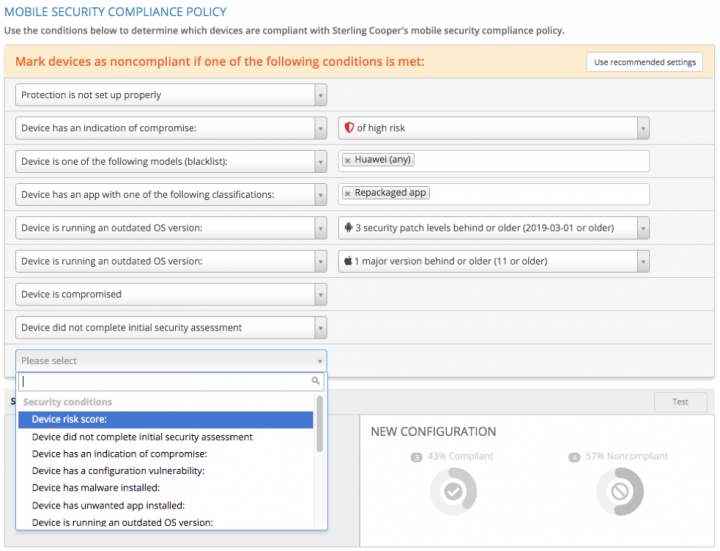
Alternatively, an organization might decide that it doesn’t want the open-remote access IoC to affect its device compliance. In this case, the organization can leave that specific IoC out of the compliance policy and select only the IoCs that it cares about. The added benefit of this is that even if certain risk factors or threats are excluded from the compliance policy, security teams don’t lose the proprietary risk insights and threat forensics provided by SEP Mobile – they continue to have full visibility over the risk landscape. If an organization decides later on to factor the threat into compliance, it can always modify the policy and use our built-in simulation tool to see how the rule will impact the install base before applying.
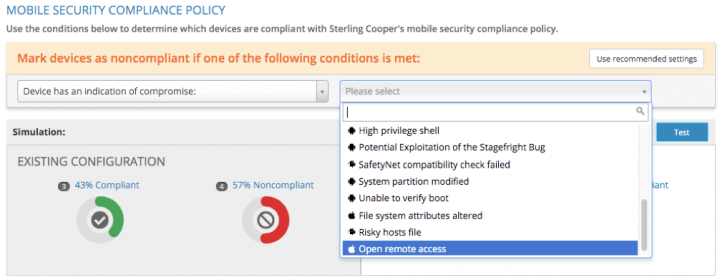
One of the biggest advantages of the compliance policy is that it covers risks beyond those stemming from device, network connection, network content and app-based threats. These include device hardware, OS version, MTD installation health, and other risk factors that do not necessarily fit into the major threat categories but can still impact the business. For example, outdated OS versions are not inherently harmful but can be exploited by malicious actors to compromise devices. Security teams can define a rule in the compliance policy that says any device running “X” versions behind the most recent one will be considered non-compliant.
Ultimately, organizations can rely on default recommended settings for their compliance policy, which are based on industry best practices, or they can edit the policy according to their specific needs.
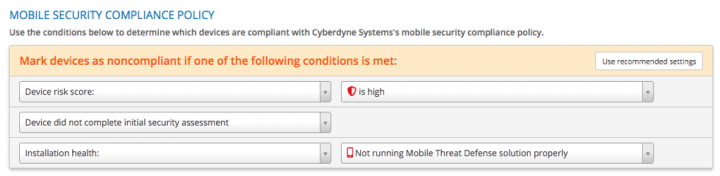
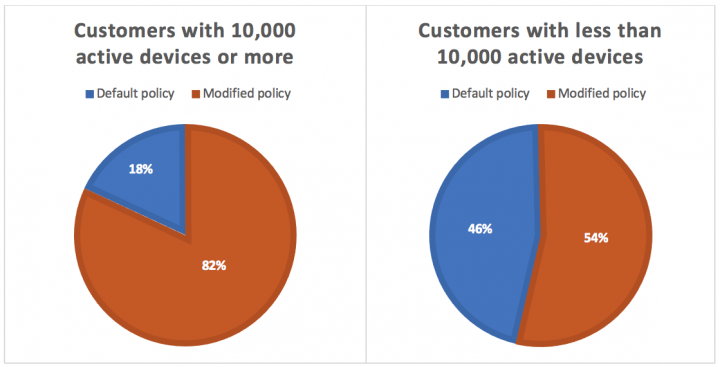
The policy includes both broad and granular conditions that organizations can customize to meet their mobile risk tolerance goals. Among our customer install base, we see that large enterprises modify the default compliance policy more often than smaller companies do. This aligns with the level of control and granularity large companies generally look for in a security solution, versus smaller teams that may prefer to use recommended policies.
Effective Policy Enforcement
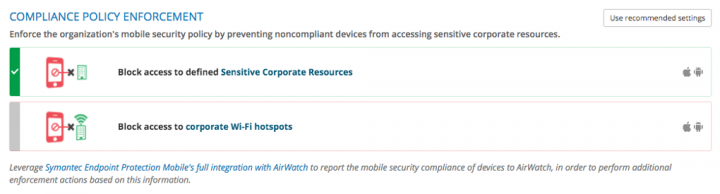
SEP Mobile customers can also use built-in, on-device actions to enforce the compliance policy. Non-compliant devices can be blocked from accessing sensitive corporate resources, with users receiving an alert to remediate the violation in order to restore access. When additional layers of enforcement are needed – i.e. when a device has been compromised – SEP Mobile provides integration with Enterprise Mobility Management (EMM) systems which allow more aggressive actions in order to achieve compliance (such as device remote wipe).
Speaking the Language of Business
Beyond making security practitioners’ lives easier on a tactical level, the compliance policy enables admins to better reflect to decision-makers if mobile security risk is aligned with business needs. Rather than talk about the technical aspect of threats, which often come across as abstract to business leaders, security teams can use the compliance policy to show if the organization is on course with its risk tolerance target. SEP Mobile provides risk metrics, including compliance levels and key risk factors, that security teams can rely on to help decision-makers understand how much mobile security risk the organization can tolerate to support business goals.
Consider it this way: If the response to threats is managed at the tactical/operational level of an organization’s security program, and business risk is managed at the strategic level, then the compliance policy sits in between them, i.e. translating threats into business risks. By aligning mobile security risk with business objectives, security practitioners can better convey the value of their programs in a language decision-makers can understand.
Dan Woods, a technology analyst and writer, describes the evolving role of CISOs today, stating, “CISOs … need a way to explain risk, and, more importantly, make everyone else in the business comfortable with it. Cyber security can never reach a state of 100% protection. There will always be tradeoffs. Therefore, CISOs need to help individuals in their companies understand this reality so that informed decisions can be made to guide the business forward.”
Tasked with this responsibility, security leaders need solutions (read: not more solutions, but better solutions) that can give them the bottom-line data to understand how mobile security threats contribute to an organization’s risk posture. Instead of focusing on whether a threat is a risky hosts file, malware, an untrusted root certificate or something else, with SEP Mobile’s compliance policy, leaders can focus on the bigger picture of mobile security in the organization. This approach can reduce cyber burnout and help security professionals become trusted risk advisors for their company.

How to Effectively Secure Hundreds of Thousands of Mobile Devices
Participants should leave this webinar with knowledge and considerations to help them evaluate mobile security solutions and plan an effective deployment and execution in their own environment.

Symantec Mobile Threat Defense: Spotlight on Mobile Endpoint Detection and Response
Organizations need mobile EDR to combat a growing trend in mobile security: advanced and persistent attacks that exploit mobile OS vulnerabilities








We encourage you to share your thoughts on your favorite social platform.