In my past couple of articles (What is Azure B2C & Multi-Tenant Architectures with Azure B2C), we talked about some of the basics of using the Azure Active Directory Business to Customer (Azure AD B2C) platform and about some common use cases.
Continuing that thought, I have a three-part series to discuss one more common use case for Azure Active Directory B2C: Consolidating User Accounts into a single Identity Provider.
In today’s world, there are so many different online services. It is common for users to have multiple accounts with different identity providers. However, managing multiple accounts can be a daunting task, and users often find it challenging to remember multiple usernames and passwords.
This is where Azure Active Directory B2C comes into play. It is a cloud-based identity and access management service that provides organizations with a secure and flexible way to manage customer identities and access to their applications and services. With Azure AD B2C, you can migrate and consolidate users from other identity provider systems.
Consolidating identity providers into Azure B2C can help simplify authentication for your customers, reduce the risk of security breaches, and improve the user experience.
Two Options for Migrating Users from External Identity Providers
In general, there are two “flavors” of migration patterns to choose from. The first is a Bulk Migration of users in one batch. This type of migration can be done with little-to-no impact to the end user as long as the user account details (such as usernames, passwords, emails, account information, etc.) are readily available in a format that can be exported to clear-text and subsequently imported into Azure B2C.
Read more on Bulk Migrations here
The second flavor of migration is a “Just In Time” migration. This particular type of migration relies on custom-built middleware integrated with B2C API connectors OR custom policies with embedded API calls as part of the authentication flow. This style of migration is the only option if you are unable to easily access the user account details from the current identity provider.
Read more on Just In Time migrations here
The approach you select depends on what data is available from the legacy provider and how much downtime your system can tolerate to complete the migration.
Consolidating Social Identity Providers
After migrating local username/password accounts, the next logical step in consolidating identity providers is to connect other social logins or enterprise accounts to the Azure identity provider.
With Azure B2C this connection is simple and straightforward. Navigating to the “Identity Providers” menu within Azure B2C shows a healthy list of external identity providers that can be easily connected into B2C and effectively consolidating all of a users many logins and accounts to a location where permissions, attributes, and settings can be managed in one single place.
From this same menu, it is also possible to add a custom identity provider:
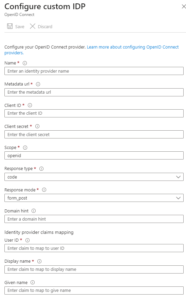
This can be used to add providers like Okta or Auth0 and allow users to use their accounts from those providers through B2C on any app in the B2C tenant!
Benefits of Consolidating Identity Providers
Azure B2C (Business-to-Consumer) is a cloud-based identity and access management service that provides organizations with a secure and flexible way to manage customer identities and access to their applications and services. Consolidating identity providers into Azure B2C can help simplify authentication for your customers, reduce the risk of security breaches, and improve the user experience.
To consolidate username/password type accounts into the B2C provider, you can employ either the Bulk Migration or the Just-in-Time approach. The approach you select depends on what data is available from the legacy provider and how much downtime your system can tolerate to complete the migration.
To consolidate social identity providers or other Oauth2.0-compatible systems, B2C provides a simple straight-forward menu directly in the tenant portal that can be used to connect any provider and start utilizing external logins across all apps within the B2C tenant.
Consolidating Identity Providers with Azure B2C can Offer Several Benefits for Organizations, including:
- Simplified Authentication: With Azure B2C, customers can use their existing social media or email accounts to authenticate into your applications, without having to remember multiple usernames and passwords. This can simplify the authentication process and reduce the risk of password-related security breaches.
- Improved Security: By consolidating identity providers with Azure B2C, you can leverage Azure’s built-in security features, such as multi-factor authentication and conditional access policies, to better protect your applications and data.
- Better Insights: Azure B2C provides analytics and reporting tools that enable you to gain insights into customer behavior and usage patterns. This can help you identify trends and improve the user experience.
- Scalability: Azure B2C is a cloud-based service that can scale to meet the needs of small, medium, and large organizations. This means that you can easily accommodate growth and handle peaks in user traffic without having to worry about infrastructure or capacity limitations.
Overall, consolidating identity providers with Azure B2C can offer a more streamlined, secure, and personalized experience for your customers, while providing your organization with greater insights and scalability.




