Never Assume Access
The foundational premise of Zero Trust is that access is never assumed. Standing privilege no longer exists. Privileged access is evaluated (and reevaluated) whenever a user (or device or application) seeks access. Each time an access request is made, the privileged access management (PAM) system evaluates contextual information such as job role, peer permissions, request history, and other identifiers to determine whether or not to grant access. If activity is deemed questionable, an alert goes out to an admin for further scrutiny.
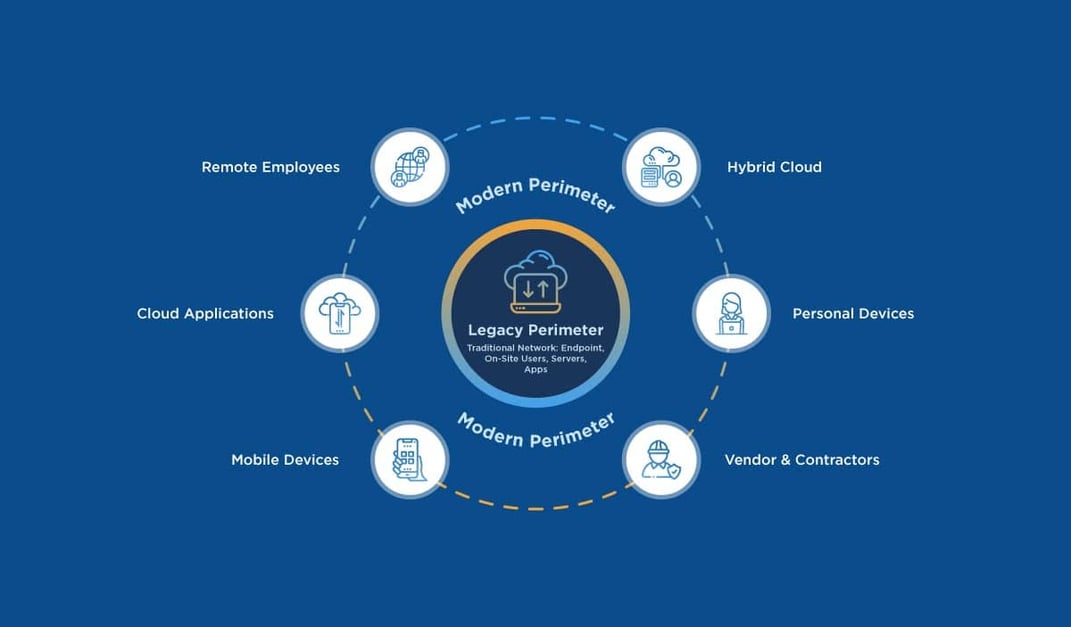
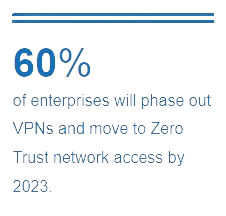
Eliminate the VPN
VPNs are quite vulnerable to compromised credentials and insider attacks, whereas security based on identity, by nature, are significantly less vulnerable and the impact is minimized. Because Zero Trust assumes all traffic is dangerous, no one is given the metaphorical key to keep for use whenever desired. Instead, access is granted only if the identifying information checks out. Ditching the VPN in favor of identity-based security allows organizations to limit the damage from insider attacks, reduce the risk presented by compromised credentials, and facilitate secure access for employees working from home.
Protect Hard-to-Secure Items
Traditional security strategies do a poor job of protecting access to web servers, cloud services, and other publicly-available items. Because Zero Trust doesn’t depend on firewalls, each of these cloud-based items can be kept secure from anyone and anything that doesn’t pass the identity evaluation. Additionally, access is granted only for the amount of time necessary for the user to complete the task at hand (which could be a matter of hours, weeks, or months). Because access is time-limited, employees who leave for another organization will no longer be able to access the CRM, PM tool, etc. after they’ve left. And if an attacker uncovers access credentials without being caught by the security system, they won’t have access for long.









.png?width=225&height=160&name=ban2%20(2).png)