10 essential tips for bolstering cloud security in your business
CIO
NOVEMBER 6, 2023
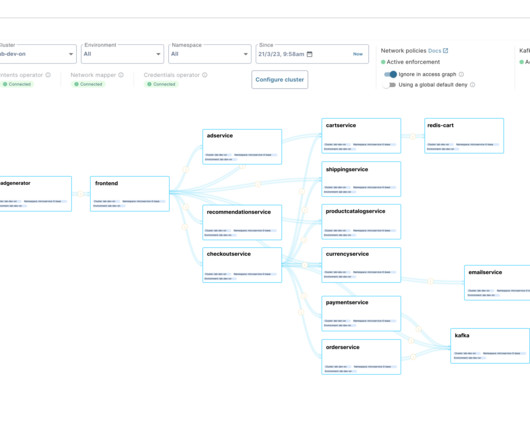
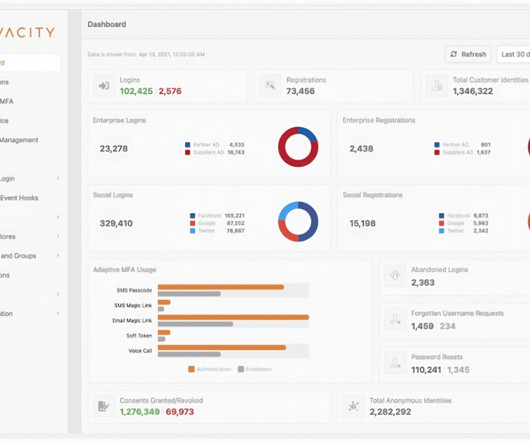
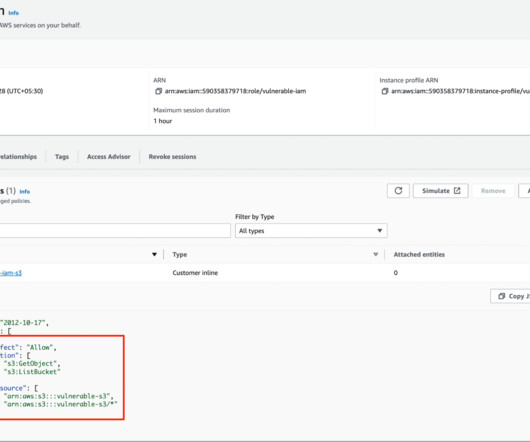
The business world is rapidly continuing its digital transformation and relying on cloud-based solutions. This makes it more critical than ever to adopt strong security measures to protect sensitive information and infrastructure. Encryption : Use encryption to protect sensitive data in transit and at rest.



















































Let's personalize your content