Publish Azure DevOps Extensions using Azure Workload Identity
Xebia
SEPTEMBER 18, 2023
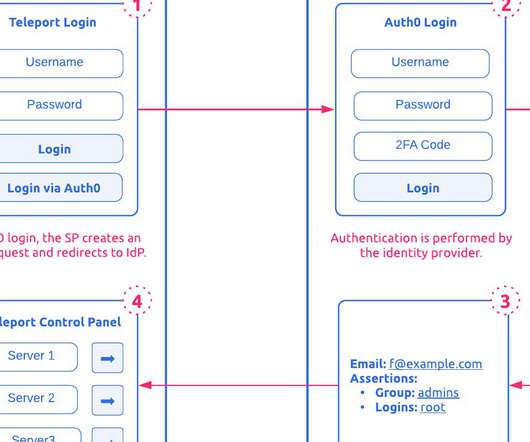
As you may know, I maintain several Azure DevOps Extensions. To publish them I use the Azure DevOps extension tasks. And to authenticate you must provide a Personal Access Token. If you need help configuring a basic CI/CD pipeline for an Azure DevOps Extension, check out the guidance on Microsoft Learn ). Learn more.












































Let's personalize your content