There is no doubt that SaaS has grown in popularity since 2020, but with all the collaborative benefits that SaaS and cloud services offer, new challenges have arisen. SaaS has become a target for attackers as a result of this rapid move to cloud SaaS environments. Organizations should assess their cybersecurity posture on all fronts. This article explores what SaaS security is, its challenges, real-life examples, best practices, and trends for SaaS security. First, let’s start with what SaaS security is.
What is SaaS Security?
Software as a Service security refers to the measures and practices implemented to protect the data and applications hosted by SaaS providers. Security measures include encryption, authentication, access controls, network security, data backup & recovery.
SaaS security is concerned with the policies and practices implemented by SaaS providers. As a result of these security policies, SaaS apps are safe and trustworthy.
Why is SaaS Security Important?
Due to the amount of confidential data in software as a service environment, they are a common target for cybercriminals. If a security breach occurs, the integrity and safety of the system are compromised, and huge losses can result.
SaaS security is, therefore, essential to protect sensitive data and prevent disasters. In contrast, if the SaaS provider fails to deliver up-to-date services, businesses may experience security threats.
For a SaaS security solution to be successful, all the top SaaS security practices must be implemented by the users or business owners. Businesses that fail to follow best practices or SaaS security solutions will be liable for any legal repercussions. Hence, an organization must focus on data security if it implements a SaaS model.
SaaS Security Risks and Challenges
Cloud-based applications and services have transformed businesses with software as a service (SaaS). While SaaS offers many benefits, it also poses many security challenges. Listed below are some of the top SaaS security challenges:
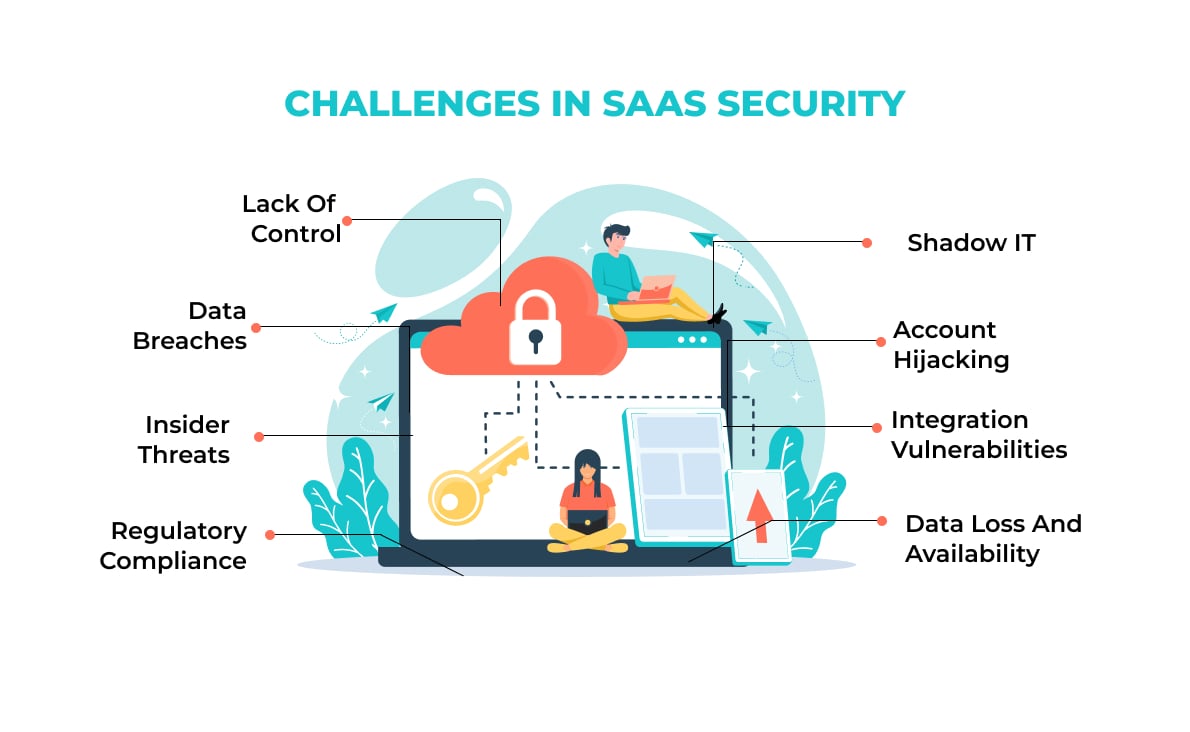
1. Lack of control
Cloud-based SaaS providers typically host data and applications, making SaaS application security less controllable for consumers. As a result, customers may find it difficult to monitor and manage their security effectively.
2. Data breaches
Many sensitive data sets are stored in the cloud with SaaS solutions. Without proper security measures, this data can be vulnerable to breaches. A SaaS provider’s infrastructure or user accounts may be exploited by attackers, resulting in data compromise.
3. Insider threats
SaaS providers have access to customers’ data, and their employees can pose insider threats. Despite stringent security measures implemented by reputable providers, the possibility of insider mishandling or accessing sensitive data remains a concern.
4. Regulatory compliance
There are different privacy and data protection laws in different industries and regions. SaaS providers must comply with these regulations before organizations adopt them. Keeping data secure, transferring data cross-border, and complying with third-party services can be quite challenging.
5. Data loss and availability
Cloud infrastructure is critical to the availability and reliability of SaaS applications. Business operations can be affected by system outages or disruptions, which result in loss of access to critical applications and data. If backup and recovery mechanisms are not in place, accidental deletion or corruption of data within the SaaS environment can result in data loss.
6. Integration vulnerabilities
In an organization’s ecosystem, SaaS applications are often integrated with other systems and services. Integrations that are not secure can be used by attackers as entry points. For unauthorized access to data and leaks of information, integrators must be assessed and monitored carefully.
7. Account hijacking
Most SaaS solutions require users to create accounts and authenticate. Using weak passwords or compromised account credentials can give unauthorized access to data, lead to data loss, or manipulate data. To prevent user accounts from being compromised, organizations need to enforce strong authentication practices.
8. Shadow IT
Individual employees or departments can adopt SaaS applications without proper supervision from IT departments since they are easy to deploy. Unauthorized and unmonitored applications may compromise data security and regulatory compliance as a result.
3 Real-life Examples of SaaS Security Breaches and Lessons Learned
Over the past ten years, cloud computing has grown from a niche industry into a cornerstone of the IT industry, enabling virtualization, storage, hosting, and other networking services to be more powerful. However, cloud environments are vulnerable to cyberattacks. 40 percent of organizations reported breaches in cloud security in 2021.
Listed below are three cloud security breach examples and lessons that every organization can learn from.
1. Facebook
Facebook reported a breach in April of 2021 that exposed hundreds of millions of user records on Amazon’s cloud service. Despite Facebook’s confirmation that the issue was identified and resolved immediately, Mark Zuckerberg was affected by the attack. There was private information contained in the database exposed that could be exploited by social engineers for targeted attacks or hacking purposes.
Learnings: Facebook reached out to Amazon to resolve this issue, which resulted in the exposed servers being taken down. “You’re not paying attention if you’re still opening AWS buckets to the public,” says business advisor Corey Quinn.
2. Cognyte
Cognyte’s cyber analytics firm left a database unsecured without authentication protocols in May of 2021. As a result, 5 billion records were exposed by hackers. Data points such as names, email addresses, passwords, and vulnerabilities within their system were exposed. Search engines even indexed the information.
Learnings: This incident illustrates how persistent cyber attackers can effectively exploit even the smallest of security flaws. The company was able to secure the data within four days, but it highlights the risk of businesses falling victim to cyber-attacks in the future. As a result, cyber attack prevention is of utmost importance. The best way to prevent attacks is to combine policies, tools, education, and vigilance.
3. Accenture
Accenture was attacked by LockBit ransomware in August 2021. It is claimed that the culprits stole 6TB of data in exchange for a ransom of $50 million. Credentials linked to Accenture customer accounts were exposed on the largest exposed server. Nearly 40,000 plaintext passwords were found in one backup database.
Learnings: AWS cloud servers should be configured correctly by IT departments and/or cyber security personnel. A misconfigured server can cause extreme reputational, client, and financial damage.
What are SaaS Security Best Practices?
An application hosted in the cloud is often secured by the SaaS provider. Among the responsibilities of the SaaS provider include securing the platform, network, applications, operating system, and physical infrastructure. However, providers are not responsible for protecting customer data. Some SaaS providers offer only the bare minimum of security, while others offer a wide range of options.
To protect data in SaaS applications, organizations can adopt the following SaaS security practices.
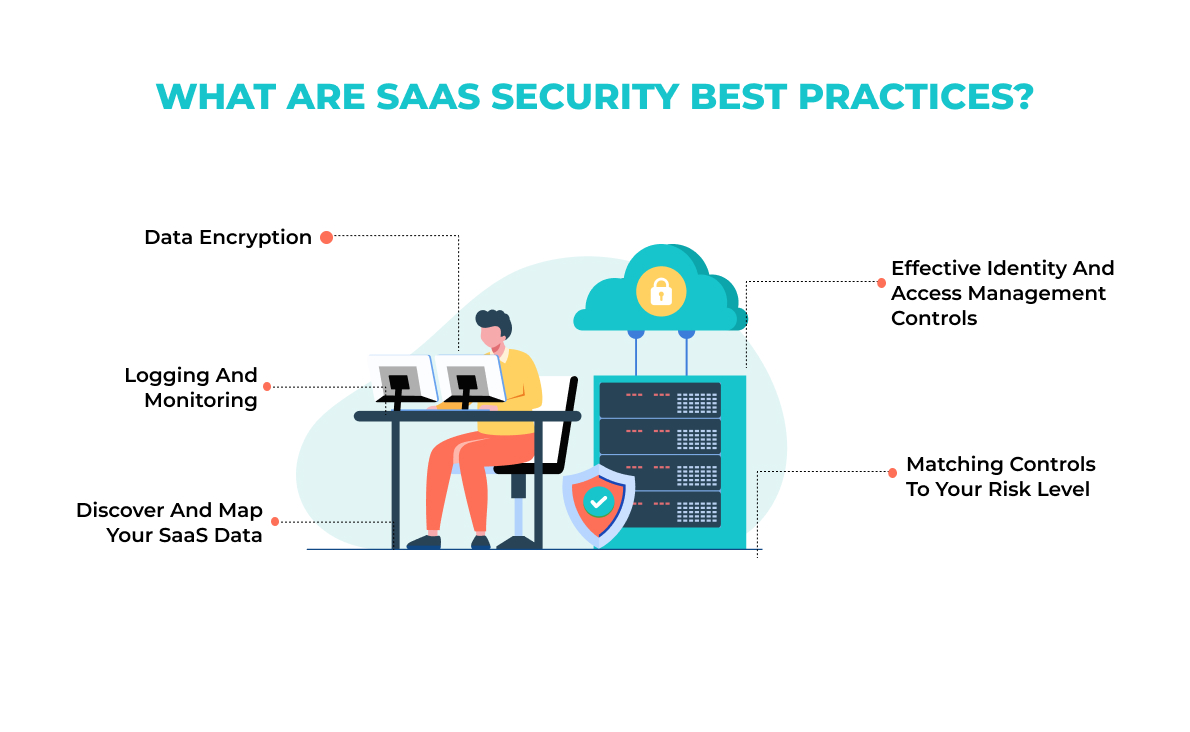
1. Data encryption
Due to the lack of traditional security methods like firewalls, cloud apps rely on encryption and key management to protect their data. Customers prefer to manage their keys through local hardware facilities rather than leave this to vendors. Transport Data Encryption (TDE) can protect data “in motion.”. However, HTTP or FTP data transfers can be risky, so Transport Layer Security (TLS) should be used to protect them.
2. Logging and monitoring
All login attempts into the SaaS system, whether successful or unsuccessful, should be logged. Data amendments are also subject to the same rules. A security plan is essential for mitigating data breaches and establishing future security arrangements.
3. Discover and map your SaaS data
A SaaS security professional should prioritize secure discovery, mapping, classification through tagging, and monitoring of all data in transit, in use, or at rest. SaaS developers must be aware of, follow, and protect shadow and unmanaged cloud data. To provide your data with the maximum level of protection, the data navigation process is essential. With the right solution, you can detect and follow your sensitive, known, and shadow data and then automate data labeling to continuously highlight valuable and sensitive data stores.
4. Matching controls to your risk level
Depending on the level of risk accepted by the SaaS vendor, security controls can be defined. SaaS providers will have to match their control over data access, processing, and monitoring against one another to optimize performance. Previously, this balance leaned toward business performance, but high-profile security breaches have shifted the pendulum back toward a more balanced approach.
5. Effective identity and access management controls
A user’s identity can be confirmed using IAM tools. Integrating with IAM tools is a key requirement for SaaS users. Enterprise users don’t want to use different passwords to access different parts of a system. An IAM system must have sophisticated access control that determines who accessed what and when.

Bonus Read: SaaS vs Cloud Computing
Future Trends in SaaS Security in 2024 & Beyond
Whether it is ransomware attacks or major data leaks, businesses are constantly reminded of the urgency to secure their data. Your business could face disaster with just a breach of credentials, a human error, or a cloud misconfiguration. Below are the top SaaS security trends for 2024 and how they can help you protect your data:
1. SaaS security posture management
SSPM prevents unintentional vulnerabilities in the SDLC. In all cloud environments, SSPM provides a unified level of transparency. This eliminates the need to verify multiple discrete endpoints from multiple vendors. By using this process, misconfigurations can be reduced while time-to-market can be increased. It regulates and automates the security of SaaS data.
2. Protecting cloud SaaS environments with AI and Machine Learning
The use of Artificial Intelligence (AI) and Machine Learning (ML) solutions significantly improves the efficiency and effectiveness of low-level security tasks. Additionally, AI and ML can better detect anomalous behavior and other malicious activity hidden under normal noise.
3. Implementing data loss protection
Investing in and implementing data leak, and data loss protection will remain a trend in SaaS security for 2024. When there are no controls or remediations in place, data leaks or loss events can cause significant harm to a company’s reputation. Without the right controls and policies, the possibility of data leaks in cloud SaaS environments is always a looming possibility. An additional risk to mission-critical data is accidental and intentional data deletion. There is a high possibility of businesses not accounting for data loss caused by their employees. The top reason to back up data is to prevent loss due to human error.
4. Automating cyber security and responses
A SaaS security trend to watch out for in 2024 and beyond is the implementation of cybersecurity automation in cloud SaaS environments to combat threats like data leaks, ransomware, insider threats, and shadow IT. Manual human effort is simply not sufficient to secure cloud SaaS environments. A cloud SaaS environment can benefit from Artificial Intelligence (AI) and Machine Learning (ML) solutions that close the cybersecurity gap.
5. Cloud ransomware protection
During the past couple of years, ransomware attacks have escalated and increased awareness of the importance of preparing for and defending against attacks. A ransomware attack makes headlines, and organizations don’t want to be associated with it. Therefore, companies are investing in AI and Machine Learning technologies to proactively detect and stop ransomware attacks as soon as possible, minimizing security risks and data leaks.
Final Thoughts on SaaS Security
It is becoming increasingly important for organizations to develop and update their risk appetite statements, build incident response plans, and perform through structured third-party risk management programs. This will gain insight into the security posture of each vendor as the SaaS model continues to expand. By assessing their complete security posture, organizations will know what risks each SaaS provider is associated with. Additionally, SaaS providers need to standardize their security processes, define clear responsibility models, be transparent with their customers, and strive for continuous improvement. If anything less is done, there will be undiscovered risks.