This is a guest article by Srushti Shah from Middleware.io
Serverless security has become a significant player in the B2B tech landscape. The market statistics speak for themselves: From a value of USD 1.4 billion in 2021, the serverless security market is projected to surge to USD 5.1 billion by 2026, reflecting a Compound Annual Growth Rate (CAGR) of 29.9%.
Furthermore, as per recent data, 21% of enterprises have already integrated serverless technology and an additional 39% are exploring its potential.
However, with this growth comes pressing security concerns. Despite the advantages, organizations face risks akin to on-premise environments, including increased attack surfaces and data breaches. This is where serverless security steps in, emphasizing behavioral protection, code safety, and stringent client-side permissions.
This blog will navigate through:
- The essential pillars of serverless security: robust authentication and authorization, ensuring data security and integrity, rigorous monitoring and logging, and safeguarding against brute force attacks.
- Established best practices, encompassing secure coding, rigorous access controls, data encryption techniques, comprehensive monitoring of serverless applications, and the integration of third-party security tools.
- A comprehensive walk-through to help organizations like yours fortify their serverless applications against threats and ensure optimal performance.
Let’s get started.
Understanding Serverless Architecture
Serverless computing, contrary to its name, doesn’t mean servers are absent. Instead, it refers to a model where the cloud service provider fully manages the execution of a developer's code by dynamically allocating machine resources.
This means that developers can focus purely on their code without worrying about the underlying infrastructure.
Benefits of Serverless Architecture
Serverless computing has gained prominence over the last decade due to its ability to reduce costs, decrease latency, improve scalability, eliminate server-side management, etc. The three primary benefits, however, include:
Scalability. One of the most enticing features of serverless is its auto-scaling capability. Unlike traditional setups, where scaling often involves manual interventions, serverless platforms automatically adjust to handle varying loads of requests.
Cost-Efficiency. Users only pay for the actual amount of resources consumed by executions, not pre-purchased units of capacity or uptime. This means no costs are incurred when your code isn't running.
Reduced Operational Overhead. As server management is handed off to cloud providers, the burden of patching, updating, and maintaining servers is eliminated, streamlining operations.
The Mechanics of Serverless Security: How Does It Work
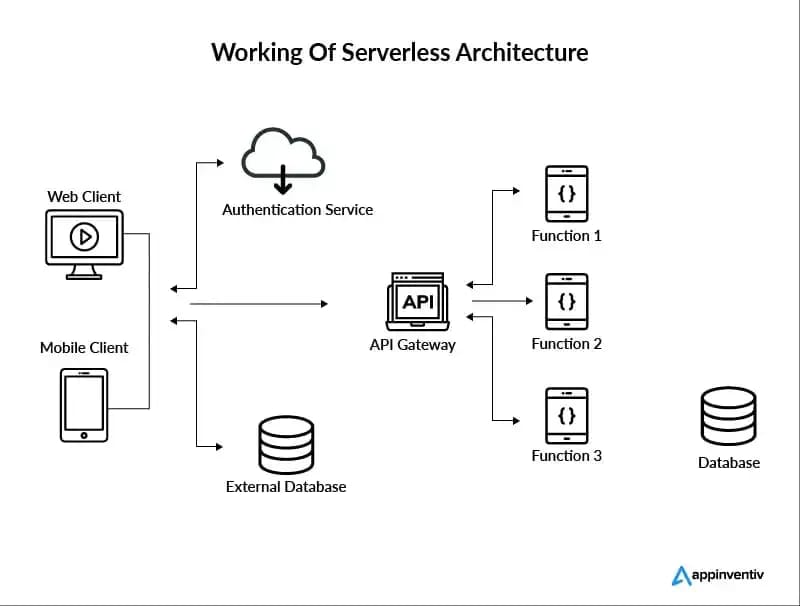
How does serverless work? Source: Appinventiv
Serverless security is an additional layer of protection added directly to the applications to secure the code functions. It thereby gives developers compliance and security posture over their applications. Here’s how serverless security works:
1. It’s Based On Event-Driven Architecture
Most serverless architectures provide a multitude of event sources that can trigger the execution of a serverless function. Specific events or triggers – like a file upload, database modification, or a new user sign-up – initiate automatic code executions.
2. The Infrastructure Is Managed by the Cloud Providers
The provider ensures that when a function is called upon, the necessary resources are allocated to execute that function seamlessly. Cloud providers, such as AWS with Lambda or Google Cloud with Cloud Functions, take on the heavy lifting. They handle server provisioning, maintenance, and scaling. This allows developers to focus on writing and deploying code.
3. Key Components of Serverless Security
Functions. These are blocks of code, usually designed to perform a single, specific task. They are invoked or executed in response to an event.
Triggers. An entity or action that initiates the execution of a function. For example, an HTTP request can act as a trigger for a function designed to retrieve data.
Event Sources. These are AWS services or developer-created applications that produce events and can serve as triggers. Popular event sources include Amazon S3, DynamoDB, and API Gateway.
Security Challenges in Serverless Environments
Traditional security protocols may fall short and require a fresh approach to safeguarding data, functions, and access controls. Let’s look at the top security challenges that serverless security faces.
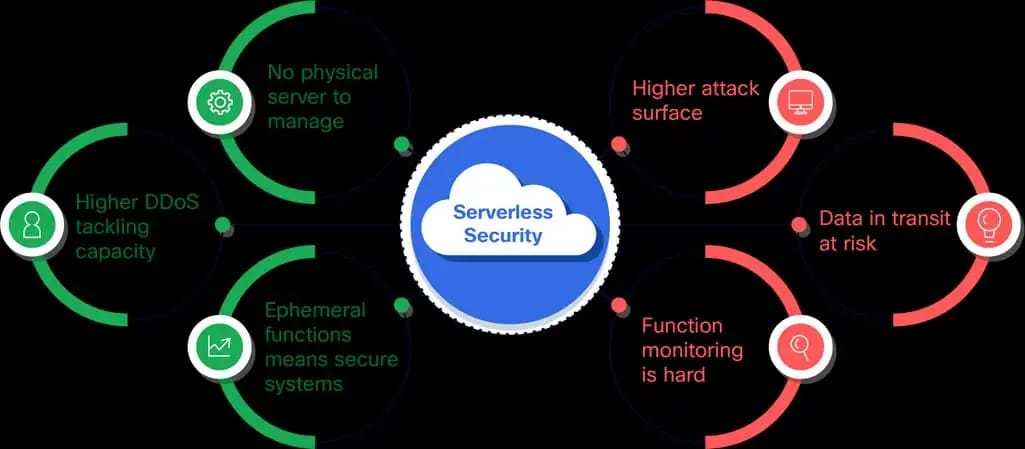
Pros and cons of serverless security Source: Panoptica
1. Data Privacy and Storage
Sensitive data handling is a major concern in serverless environments as they face the potential for breaches or unauthorized access. For example, the Accenture Cloud Platform was found to have exposed internal AWS API keys, risking sensitive information.
Storing plaintext data can be a direct invite to breaches; hence, encryption at rest and in transit is non-negotiable. Companies must also consider solutions like AWS Key Management Service or Azure Key Vault to manage cryptographic keys to empower their data protection mechanisms.
2. Function Security
The dynamic nature of serverless also opens doors for attacks such as code injection. One prominent instance is the Capital One hack, where a misconfiguration in a web application allowed a former AWS employee to exploit and gain access to over 100 million customer accounts.
To prevent such vulnerabilities, proper input validation is crucial to ensure that harmful or unexpected data doesn't breach the system. Further, you can use output encoding to sanitize any data returned by the server.
Moreover, third-party dependencies (which serverless apps often rely on) need stringent monitoring and management.
3. Authentication and Authorization
To put it into perspective, improper access controls in serverless apps can be compared to leaving the front door of a house wide open. Take the case of a serverless application that doesn’t validate user tokens properly, granting attackers a way in.
Implementing Role-Based Access Control (RBAC) in serverless applications ensures that functions and data are only accessible to entities with the appropriate permissions.
Furthermore, integrating with Identity and Access Management (IAM) systems works as an additional layer of security. These systems allow for meticulous management of user access by giving administrators granular control over user action.
Best Practices for Serverless Security
Serverless architectures, while revolutionary, are not exempt from security threats. It requires a blend of traditional security wisdom and innovative practices tailored to the serverless ecosystem. Let's delve into four best practices to fortify your serverless applications.
1. Least Privilege Principle
The principle of least privilege (PoLP) is a foundational cybersecurity tenet, advocating that any process, user, or application should only be granted the bare minimum permissions necessary to perform its task. Businesses can significantly mitigate the risk of unauthorized data access or system exploits by adhering to this principle.
Let's picture a serverless function meant only for data logging. Instead of granting it indiscriminate database write access, its permissions should be precisely calibrated to append logs only. When dealing with a function related to customer payments, the principle would restrict its view to merely the billing segment of a user's profile.
2. Secure Deployment
The deployment phase is a critical juncture where many security vulnerabilities can either be plugged in or overlooked. Integrating automated deployment pipelines fortified with security checks ensures that code progresses to production only after thorough vetting.
For instance, a financial institution might use Jenkins or CircleCI to automate its deployment processes, incorporating tools like Checkmarx or OWASP Zap for dynamic application security testing.
Leveraging Infrastructure as Code (IaC) tools aid organizations in deploying consistent and secure infrastructure templates. A retail chain, for example, could use IaC to replicate a secure serverless environment across various regional branches, ensuring uniformity and compliance.
Additionally, employing serverless-specific security tools enhances security by tailoring the scanning process. They can detect vulnerabilities in real-time, be it a misconfigured AWS Lambda function or a poorly set API Gateway.
3. Monitoring and Logging
Real-time monitoring becomes crucial in serverless architectures, where components dynamically scale and react to events. Organizations can quickly detect anomalies, ensuring that the transient nature of serverless functions doesn't obscure potential threats.
Imagine a B2B travel platform where a surge in serverless function triggers occur. Without real-time monitoring, a malicious event—like unauthorized data access—could be lost in the flood of legitimate processes.
Centralized logging further complements monitoring by aggregating logs from disparate sources into a unified location. It streamlines incident response, as security teams can swiftly trace the origin and nature of a threat.
For instance, for a global company, centralized logging ensures that a security event in an Asian data center can be instantly relayed and analyzed at their European headquarters.
To bolster these efforts, utilizing the monitoring services provided by cloud platforms is essential. Integrating third-party tools can also enrich the depth and breadth of monitoring. It can ensure that serverless environments remain both performant and secure.
4. Serverless-Specific Considerations
Serverless architectures come with unique characteristics that necessitate tailored security measures. A notable aspect is the "cold start" - when a function initializes after being idle. This period can introduce vulnerabilities, especially if initialization involves sensitive operations like database connections.
Furthermore, container reuse, a feature in many serverless platforms, can be a double-edged sword.
- On one side, it improves performance by reusing resources.
- But on the flip side, it can inadvertently retain data from previous executions.
A cloud-based CRM, for instance, might inadvertently retain and expose customer data if containers are reused without proper isolation. Organizations must ensure strict container isolation protocols to guarantee data integrity and privacy in their serverless applications. They can do this by employing platform-specific settings or third-party solutions.
Case Studies: Serverless Security in Action
Let’s dive into some practical scenarios and see how your business can navigate the challenges using serverless security strategies.
A. Secure Serverless API
A fintech startup wanted to launch a new feature within its app, relying heavily on serverless APIs. To ensure secure transactions and data queries, they designed their API functions to include in-built validation, thwarting common API attacks like SQL injection.
They incorporated OAuth 2.0, ensuring both authentication (verifying users) and authorization (assigning permissions). As a result, despite handling millions of requests daily, the API maintained a sterling security record. It offers robust defense against breaches, man-in-the-middle attacks, and other common API threats.
B. Real-time Image Processing
A B2B digital asset management platform sought to offer instant asset optimization for its clients. Adopting a serverless framework, the platform processed images in real-time as clients uploaded their digital materials. A robust security filter was integrated at the upload stage, rejecting potential threats.
During processing, unnecessary metadata was stripped, and asset data was encrypted. Moreover, serverless event triggers ensured automated optimization for various uses and formats immediately upon upload. This setup provided a seamless and secure experience.
Future Trends in Serverless Security
As enterprises embrace serverless, the security landscape is witnessing a surge in innovative solutions to protect these unique infrastructures. Here's a glance at two major trends we anticipate in the realm of serverless security.
1. Enhanced Security Services
What's Changing? As more companies use serverless technology, cloud providers are stepping up their game. They're not just improving the usual features; they're making sure everything is safer too.
Big names like AWS and Azure are using smart tools powered by AI to spot and stop threats even before they can cause harm. It's like having a security guard who can predict problems and deal with them instantly. This helps keep serverless systems safe and running smoothly.
2. Serverless-specific Security Tools
What's Changing? The rise in serverless has paved the way for security tools specifically tailored to meet the distinct characteristics of serverless architectures.
Several companies have come up with solutions that cater specifically to these characteristics. These tools help businesses protect their serverless functions, manage access rights better, and maintain strong security standards against today's threats.
Conclusion
Reflect on this for a moment: many once-leading businesses, despite their resources, fell victim to security breaches because they were complacent. It's an alarming reality that even today, as technology advances at lightning speed, many organizations are caught off guard.
While embracing serverless is a stride towards modernization, it's also an open invitation to new vulnerabilities if not safeguarded correctly.
It's crucial—urgent even—to take decisive action. Harnessing the power of serverless requires a steadfast commitment to security. Adopt robust serverless security practices today and safeguard your organization tomorrow. The next steps you take could define your company's legacy. Choose wisely.

Srushti Shah is an ambitious, passionate, and out-of-the-box thinking woman having vast exposure in Digital Marketing. Her key focus is to serve her clients with the latest innovation in her field leading to fast and effective results. Working beyond expectations and delivering the best possible results is her professional motto. Other than work, she loves traveling, exploring new things, and spending quality time with family. Reach out to Srushti Shah on Twitter or LinkedIn.
