Cloud-native cybersecurity startup Aqua Security raises $60M and remains a unicorn
TechCrunch
JANUARY 3, 2024
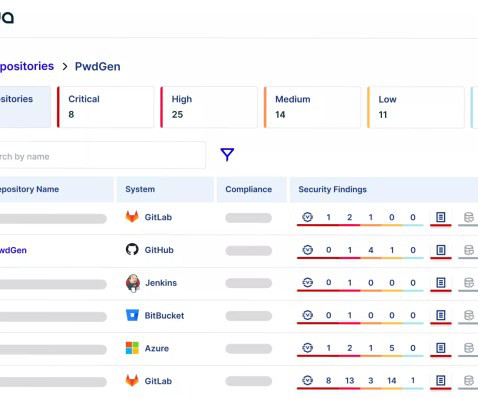
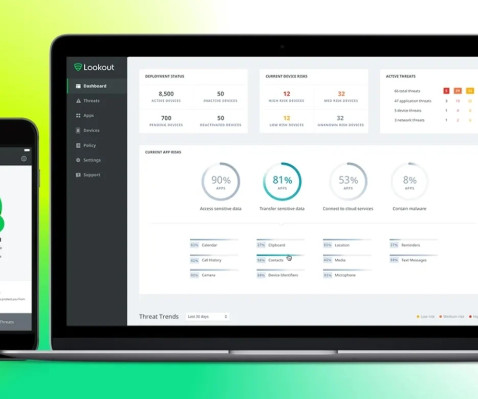
Aqua Security, an Israeli cybersecurity startup that helps companies protect their cloud services, has raised $60 million in funding, extending its previously announced $135 million Series E round of funding to $195 million.




















































Let's personalize your content