Trivy, the all-in-one open source security scanner, can scan your Kubernetes cluster as well as its running workloads for security issues. Trivy also has a native Kubernetes Operator for complete Kubernetes security posture management. These capabilities were covered in detail in our previous blog post Vulnerability Scanning: Trivy vs the Trivy Operator. This week, just in time for Kubecon, we have released Trivy v0.33 which includes a much-requested feature of compliance scanning and, specifically, an NSA hardening guide.
NSA hardening guide
NSA, the U.S National Security Agency, has released a guide for hardening your Kubernetes cluster in which they detail a set of changes that should be made to different resource types to reduce the likelihood of attacks.
NSA scans can then check whether the resources scanned are deployed following those best practices laid out in the guide.
You can learn more about the NSA guidelines in the following blog A Closer Look into the NSA Kubernetes Hardening Guide.
Tutorial
The NSA compliance scan is part of the trivy k8s command which is used to run a general security scan of all the workloads and cluster components it can find.
An additional flag can be passed into the scan to generate an NSA compliance report:
trivy k8s cluster --compliance=nsa –-report summary
You can use the compliance flag together with familiar Trivy flags to further customize the output. For example
trivy k8s cluster --compliance=nsa --report summary --format table
The --report summary flag tells Trivy that we want to get an overview of the number of findings rather than a detailed report.
The --format table flag will display the results in a table within the terminal:
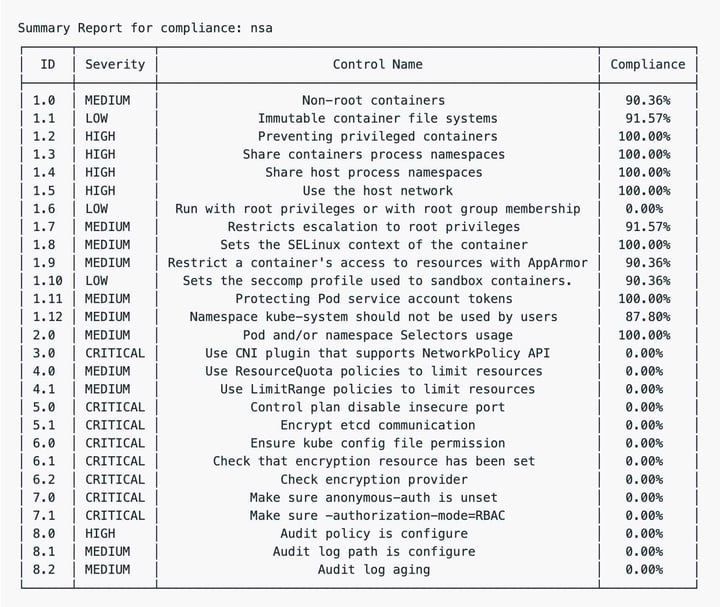 NSA compliance scan as report summary
NSA compliance scan as report summary
Alternatively, the following flags configuration will generate a fully detailed report in json format:
trivy k8s cluster --compliance=nsa --report all --format json
We can also save the result in a file; this is done with the --output flag:
trivy k8s cluster --compliance=nsa --report all --format json --output nsa-scan.json
Trivy compliance flag
We designed the --compliance flag to be generic enough to be extended to other compliance frameworks as well. Trivy’s compliance flag lets you outline a report that curates a specific set of checks. In a typical Trivy scan, we make hundreds of different checks for many different components and configurations, but sometimes you already know which specific set of checks that you want to verify. Often this would be an industry accepted set of checks such as the NSA guide, or the popular CIS benchmarks, or some other vendor specific guideline that you want to comply with. These are all possible using the flexible compliance infrastructure that we’ve built into Trivy. Compliance reports are defined as simple YAML documents that select which existing checks contribute to the report score.
Currently, we are shipping NSA compliance as a first step but look forward to seeing more compliance frameworks being added soon, as well as used, in more targets (such as Trivy AWS scanning). We will also be opening up to custom compliance reports defined and loaded locally in future releases. What’s next?
Get involved
Make sure to try Trivy and tell us what you think. And don't forget to give Trivy a Star on GitHub - it would mean a lot to us and our team of contributors!
Also, let us know which compliance frameworks you would like to see, and, if you’re up for a challenge, contribute it to Trivy! It’s as simple as writing a YAML file, and we’d be glad to assist.
Finally, if you’re already using Trivy and a Kubernetes user, do try out the Trivy Operator. The Trivy Operator will monitor the running resources inside of your cluster on a continuous basis and generate security reports.