Invert a Binary Tree – Recursive and Iterative Approach in Java
The Crazy Programmer
FEBRUARY 21, 2021
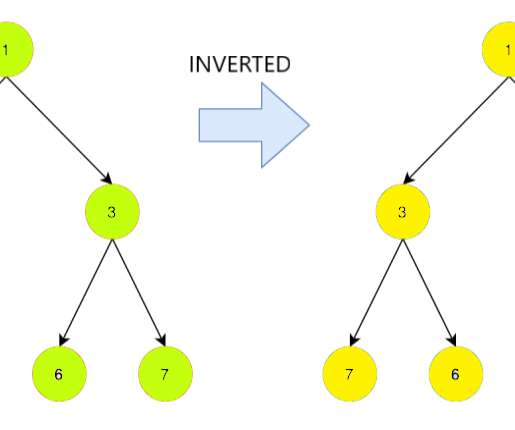
In this article we have a look at another interesting problem related to binary tree. Given a binary tree we have to invert the tree and print it. We discuss different approaches to solve this problem along with their time and space complexities. The inversion of a binary tree or the invert of a binary tree means to convert the tree into it’s Mirror image.


















Let's personalize your content