Agile vs Waterfall: Key Differences And Definition?—?Which Model Is Better?
Codegiant
APRIL 14, 2020
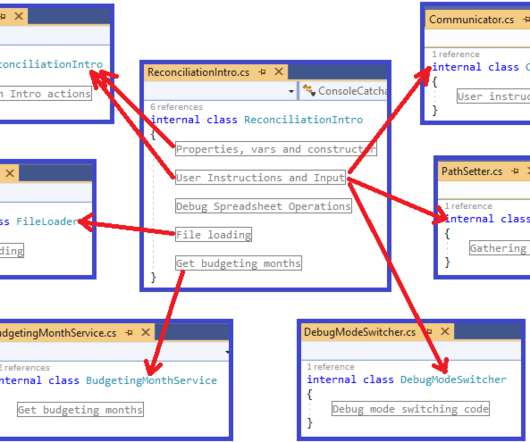
Agile vs Waterfall: Key Differences And Definition?—?Which Model Is Better? Picking the right method for managing your tasks can either make or break the success of your projects. Either you’ll produce twice more work, or you will miss your deadlines. In this article, you’ll find out whether Agile or Waterfall is more suitable for your team. NOTE: If you are running late, you can check the simple infographic below?










































Let's personalize your content