Burp Suite is a renowned testing tool that offers a wide range of features for professionals seeking to analyze and secure web applications. Among its many capabilities, the Sequencer stands out as a powerful tool for assessing the quality of randomness and predicting session tokens.
In this blog, we will delve into the Sequencer in Burp Suite, exploring its functionalities, practical applications, and how it can enhance your web security assessments.
I. Understanding the Sequencer:
The Sequencer in Burp Suite is a sophisticated tool designed to analyze the quality of randomness in data, specifically focusing on session tokens, cookies, and other sensitive information. It employs statistical techniques to identify patterns and weaknesses that attackers might exploit.
II. Practical Applications:
- Session Token Analysis:
The Sequencer can be used to evaluate the randomness of session tokens generated by a web application. A strong session token should be unpredictable, making it difficult for attackers to guess or brute-force. By analyzing session tokens with the Sequencer, you can identify weak tokens that might put your application at risk. - Password Reset Tokens:
When a user requests a password reset, they often receive a token via email. These tokens should be random and hard to predict. The Sequencer can help you assess the strength of these tokens, ensuring that password resets are secure. - Cryptography Testing:
If your web application relies on cryptographic functions, such as encryption or hashing, the Sequencer can help evaluate the quality of the randomness in keys and salts used for these operations. Weak cryptography can lead to vulnerabilities, and the Sequencer can help you spot these weaknesses.
III. How to Use the Sequencer:
1: Launch Burp Suite:
- Start by launching Burp Suite if you haven’t already. Make sure you have the professional version, as the Sequencer is not available in the free edition.
2: Configure Your Browser:
- Configure your web browser to route traffic through Burp Suite. This is typically done by setting up a proxy. Ensure that Burp Suite’s proxy listener is active and running.
3: Visit the Target Application:
- Open your web browser and navigate to the target application you want to assess with the Sequencer.
4: Capture Traffic:
- In Burp Suite, go to the “Proxy” tab and make sure the “Intercept” feature is on.
- Perform actions in the web application that generate the data you want to analyze. This can include logging in, generating session tokens, or interacting with sensitive functionalities.
5: Review Intercepted Requests:
- As you perform actions in the web application, Burp Suite will capture the corresponding HTTP requests in the “Intercept” tab. Review these requests and select the ones that contain the data you want to analyze, such as session tokens or cookies.
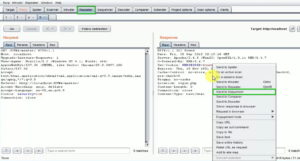
Fig: Intercepted request sending to Sequencer
6: Send Data to the Sequencer:
- After selecting the relevant requests in the “Intercept” tab, right-click and choose “Send to Sequencer.” This action will transfer the captured data to the Sequencer tool for analysis.
7: Configure Sequencer Options:
- In the Sequencer tool, you can configure options such as the analysis type (e.g., token analysis, custom character set), the number of tokens to analyze, and the statistical tests to perform. Customize these settings based on your specific assessment needs.
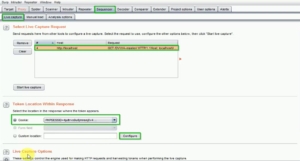
Fig: Configuring Sequencer
8: Start Analysis:
- Click the “Start Live Capture” to begin the process of analysis. The Sequencer will start examining the data for randomness and patterns.
9: Monitor Analysis Progress:
- The Sequencer will display real-time statistics as it analyzes the data. Keep an eye on parameters such as entropy, chi-squared results, and token length distribution. These metrics will help you assess the randomness of the data.
10: Review Results:
- Once the analysis is complete, review the results provided by the Sequencer. Look for patterns or weaknesses in the data, as identified by the tool.
11: Interpret the Findings:
- Interpret the Sequencer’s findings to identify potential vulnerabilities or areas of concern. Low entropy values, abnormal token length distributions, or patterns in the data may indicate areas that require further investigation or mitigation.
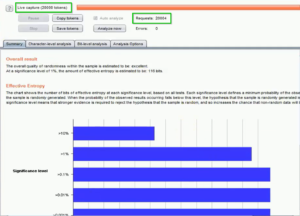
Fig: Sequencer report analysis
Step 12: Take Action:
- Based on the Sequencer’s analysis, take appropriate actions to address any identified weaknesses. This may involve strengthening session token generation, improving randomness in cryptographic operations, or implementing additional security measures.
Step 13: Document and Report:
- Document your findings and the actions taken to enhance security. This information is essential for reporting and compliance purposes.
IV. Enhancing Web Security:
By using the Sequencer in Burp Suite, you can enhance the security of your web applications in several ways:
- Identify Weak Tokens: Discover session tokens or other data elements with low entropy, which may be prone to predictable patterns or attacks.
- Improved Cryptography: Ensure that cryptographic operations rely on strong, random keys and salts to prevent potential vulnerabilities.
- Custom Testing: Tailor your testing to focus on specific tokens or data elements critical to your application’s security.
Conclusion
In the world of web security, the Sequencer in Burp Suite is a valuable tool that aids in the assessment of data randomness and the prediction of session tokens. By using this tool effectively, you can identify vulnerabilities, strengthen cryptographic implementations, and ultimately fortify your web applications against potential attacks.
Embrace the power of the Sequencer to enhance your cybersecurity efforts and keep your web assets safe from threats.

