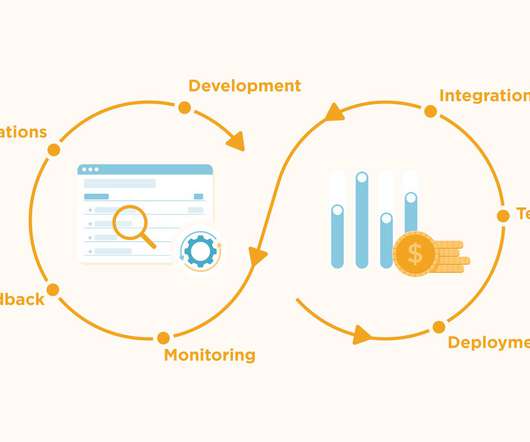
Threat Modeling as a DevSecOps Practice
DevOps.com
JUNE 17, 2022
Software engineers are always under pressure to build more software, faster. At the same time, there is increasing regulatory and market pressure for secure software that meets users’ and regulators’ requirements for data privacy. This dynamic often puts software engineers at odds with application security or product security teams. In fact, 81% of developer teams […].







































Let's personalize your content