Interception Proxy is one of the most important and useful features of Burp Suite, a popular web application security testing tool. It allows security testers to intercept and modify web traffic between a web browser and a web server. It gives them complete control over the flow of data.
Interception Proxy in Burp Suite enables security testers to intercept and modify HTTP/HTTPS requests and responses, enabling them to analyze and manipulate the data being sent and received by the web application. This makes it possible to test the security of the application by simulating attacks and vulnerabilities and then analyzing the results.
You can configure the Interception Proxy to work in different ways depending on your testing needs. For instance, you can set it to intercept all traffic between the browser and server or only traffic that meets specific criteria, like a certain URL or parameter value.
Let’s say you are a security tester and you are testing a web application that allows users to log in using a username and password. You suspect that the application may be vulnerable to SQL injection attacks, and you want to intercept the login request to modify it and test your hypothesis.
Use the Interception Proxy in Burp Suite
To do this, you can use the interception proxy in Burp Suite. Here’s how:
- Open Burp Suite and click on the “Proxy” tab.
- Click on the “Intercept” sub-tab.
- In your web browser, configure the proxy settings to use Burp Suite as the HTTP and HTTPS proxy. In most browsers, this can be done by going to the settings or options menu and entering the Burp Suite proxy address and port (usually 127.0.0.1:8080).
- Navigate to the login page of the target application in your browser.
- Enter a valid username and password in the login form, and click the “Login” button.
- Burp Suite will intercept the login request before it is sent to the server. In the “Intercept” tab, you can view the request and response headers and body.
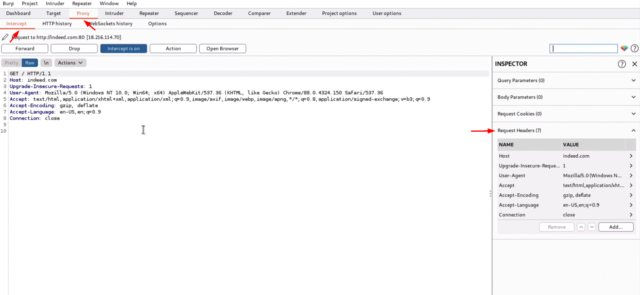
Fig 1: Interception Tab in BurpSuite
- To modify the request, simply click on the “Action” button and select “Do Intercept” or press “Ctrl+Shift+I” on your keyboard. This will pause the request and allow you to modify the parameters.
In the “Intercept” tab, you can modify the parameters of the request, such as the username and password. As a result, you can modify the username parameter to include a SQL injection payload. This will allow you to test the application’s vulnerability to SQL injection attacks. - Once you have made the desired modifications, click the “Forward” button to send the modified request to the server.
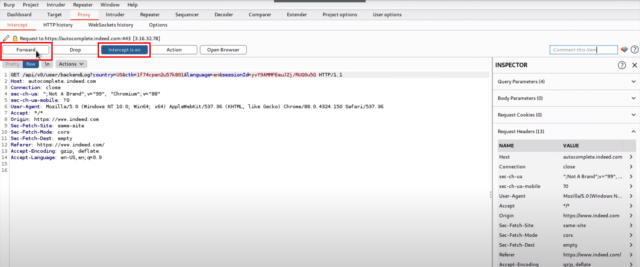
Fig 2: Forwarding modified request to the server.
- Burp Suite will intercept the server’s response to the modified request, allowing you to analyze the results.
Features of Interception Proxy
One of the most useful features of Interception Proxy is the ability to modify HTTP/HTTPS requests and responses in real time. Security testers can modify the data being sent and received by the web application, which can be useful for testing different scenarios and analyzing the application’s behavior.
For example, a security tester could modify an HTTP request to include a SQL injection attack. And then observe how the application responds to this attack. This can be a powerful way to identify vulnerabilities and weaknesses in the application.
Another useful feature of Interception Proxy is the ability to save and load traffic to and from files. This allows security testers to save traffic to a file, modify it as needed, and then load it back into Burp Suite for further analysis. This can be useful for testing different scenarios and analyzing the behavior of the application under different conditions.
Conclusion
Interception Proxy in Burp Suite is a powerful and essential tool for security testers. If the tester needs to test the security of web applications. It provides complete control over the flow of data between the client and server. Allowing testers to analyze and manipulate traffic in real time. With its powerful features and flexibility. Interception Proxy is an essential tool for any security tester who needs to ensure the security of web applications.

