FlexDeploy platform provides easy to configure role-based security model. In my experience, most FlexDeploy customers integrate with corporate directory like Active Directory. This helps eliminate user administration in FlexDeploy. In addition, FlexDeploy customers have also requested support for Single Sign-On (SSO) and Multi Factor Authentication (MFA).
Let’s review these terms first.
- Single Sign-On – once user authenticates themselves, Single Sign-On solution automatically logs them in to subsequent applications. This allows users to have one single password for all applications and avoids manual login during course of work day.
- Multi Factory Authentication – provides additional layer of security by requiring one or more piece of information in addition to password. For example, token, one time password, hardware device etc.
Single Sign-On and Multi Factor Authentication can be used together or independently, but when used together it creates convenient and robust login process.
FlexDeploy application can also be protected by such access control solutions. You can accomplish such integrations using options like OpenID Connect, SAML, OAuth etc. You can use external service like Okta, Microsoft Azure AD, and many more or use existing corporate solution. Note that FlexDeploy does not provide SSO and MFA services, rather integrates with such solutions.
Review finer details of such integration at FlexDeploy Documentation. We recommend use of Open ID Connect which is supported by many providers.
Let’s see this in action. Let’s assume we have completed necessary configuration to integrate FlexDeploy with Okta.
This paper compares FlexDeploy to other commercial and open-source DevOps and Application Release Automation solutions.
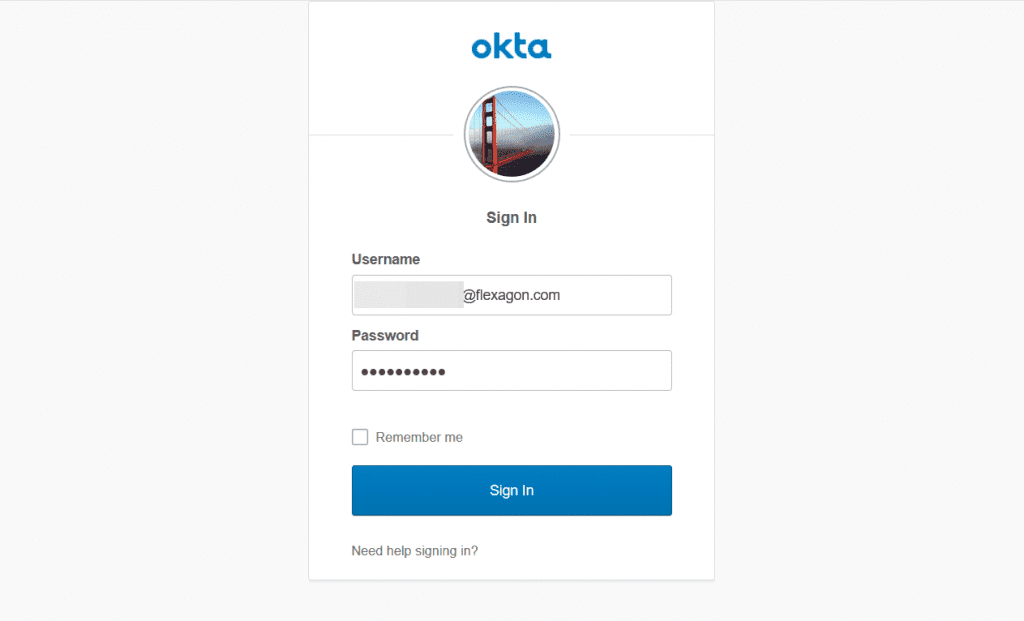
I will launch application using http://host:port/flexdeploy, but instead of traditional FlexDeploy login page, I am presented with Okta login page.
Let’s go ahead and click Sign In button after entering credential details.
On successful login using Okta, FlexDeploy is launched for specific user. At this point application will behave same as if user was created in local realm.
At this point, if you launch other applications that are controlled using same Single Sign-On solution, you will not have to provide credentials. Also, if you launch FlexDeploy after authenticating against SSO solution, you will not be prompted with login page.
We’d welcome the opportunity to show you how this integration as well as our other robust security features work.