Branching Patterns: Release Branch
Martin Fowler
MAY 6, 2020
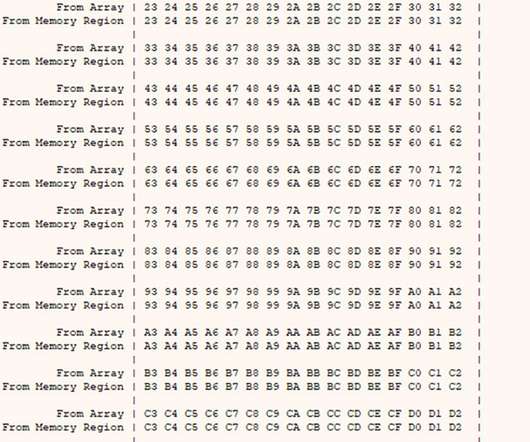
Today I begin the next section of patterns, which look at the path to production. The first pattern in this group is Release Branch: A branch that only accepts commits accepted to stabilize a version of the product ready for release. more….










































Let's personalize your content