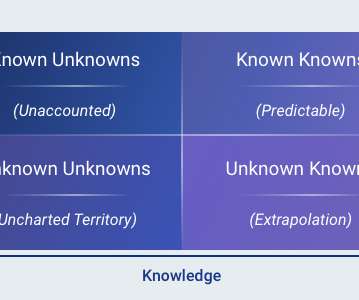
Continuous Reliability: Handling ‘Known Unknowns’ and ‘Unknown Unknowns’
OverOps
APRIL 16, 2020
Know your unknowns with the help of continuous reliability. Let’s rewind to the year 2002 (this should give you an idea of how long I have been working in software development). Mr Donald Rumsfeld, then United States Secretary of Defense, had this to say in response to a question: . While this statement was not made in reference to software, the underlying principles are applicable to the way we think about software troubleshooting.










































Let's personalize your content