Predicting the unpredictable: How attack path analysis simplifies cloud risk management
Modern cloud security is making huge leaps in the area of risk management. And while you can’t predict the future, you can ensure that your team focuses on the cloud security risks that truly matter. Here’s how.
Lacework expanded attack path analysis now generally available
In April, Lacework announced major cloud risk management enhancements to our industry-leading cloud-native application protection platform (CNAPP) — enhancements that can cut your critical alerts by up to 90%. In addition to our custom risk-based vulnerability scoring feature, Lacework released some exciting new enhancements to our generally available attack path analysis capabilities.
Attack path analysis from Lacework helps customers gain immediate visibility into their top risks and potential attack paths. It’s like seeing your cloud environment through the eyes of an attacker, identifying the easy targets and mapping out how each threat can be exploited to breach a cloud environment. As of April 2023, users can also see which critical data assets can be reached either directly or indirectly via other risky entities.
How do we do it? Our CNAPP correlates risk data from both agent-based and agentless assessments to deliver a contextualized and relevant security view. While agents help get visibility into runtime information, agentless scanning performs more data-intensive tasks to extract critical information such as vulnerabilities, exposed secrets, and identity and access management (IAM) roles.
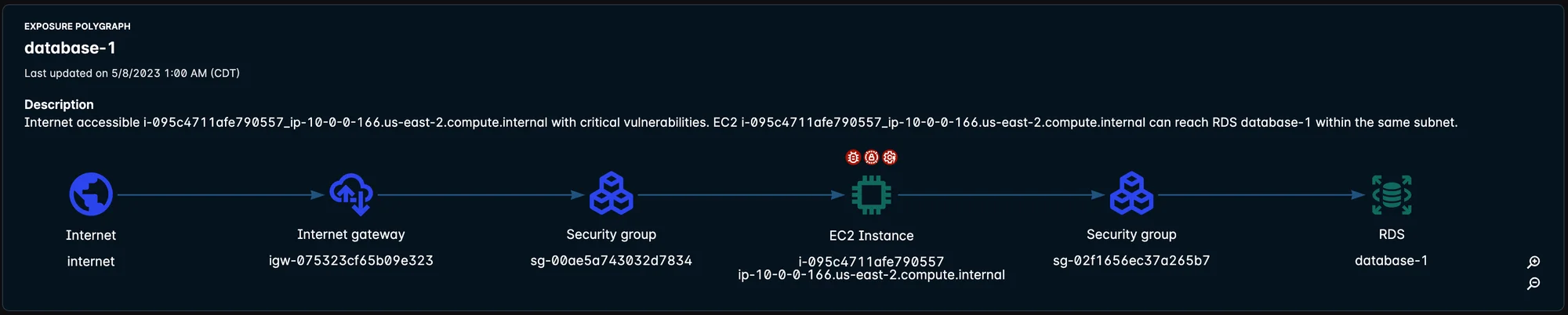
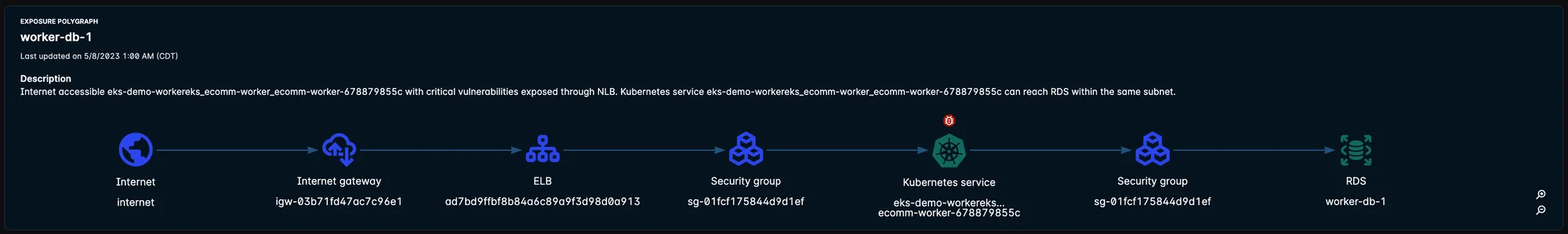
As a part of our attack path capabilities, our Exposure Polygraph visualization displays potential multi-hop attack paths, from the first publicly reachable host or container to critical data assets such as AWS RDS and Aurora. By tying together multiple risk factors such as internet-exposed hosts or containers, critical vulnerabilities, misconfigurations, exposed secrets, IAM roles, open ports, and more, the Exposure Polygraph provides a comprehensive view of the security posture.
Figure 1: Exposure Polygraph shows the first publicly reachable host or container to critical data assets such as AWS RDS and Aurora.
Attack path analysis extends to dedicated dashboards… and Kubernetes
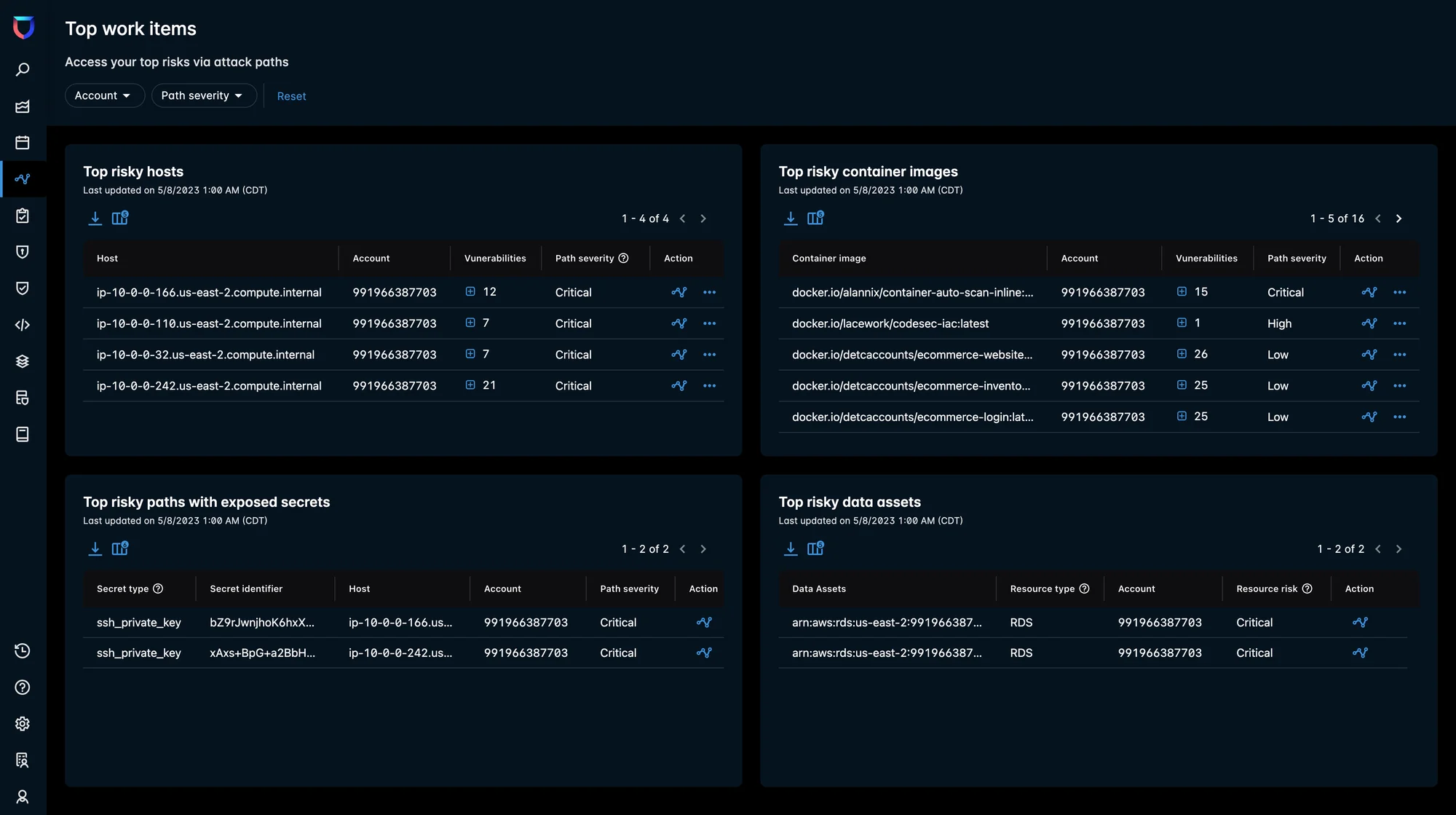
Prior to the April launch, attack path information and Exposure Polygraph visualizations were isolated to their affected alerts. Now, this information is featured in a new, dedicated attack path analysis dashboard. The unified dashboard provides immediate visibility into the top work items (the items that reduce the greatest risk to your cloud environment), as well as the most exploitable attack paths leading to your critical data assets.
Top work items
This dashboard features the most risky hosts and container images, top paths with exposed secrets, and the most risky data assets that are either exposed to the internet directly or that can be accessible via internet-exposed hosts with critical vulnerabilities and other risks. A click into any of these items surfaces the applicable attack path, as well as other contextual information.
Your security posture teams can easily understand where to focus first and effectively prioritize the most impactful work items that will reduce your risks. From this screen, your SOC teams can also dig deeper into the platform to gain more path investigation information.
Our customers are already reaping the rewards of this dashboard. In one customer’s environment, Lacework found that there were 256 attack paths leading to an RDS database. Attack path analysis revealed that 254 of those potential attack paths were possible due to one internet-exposed host with critical vulnerabilities. Lacework automatically surfaced this host as one of the top work items, making it easy for teams to quickly prioritize patching. This ultimately helped the organization drastically reduce their attack surface and risks with a single remediation.
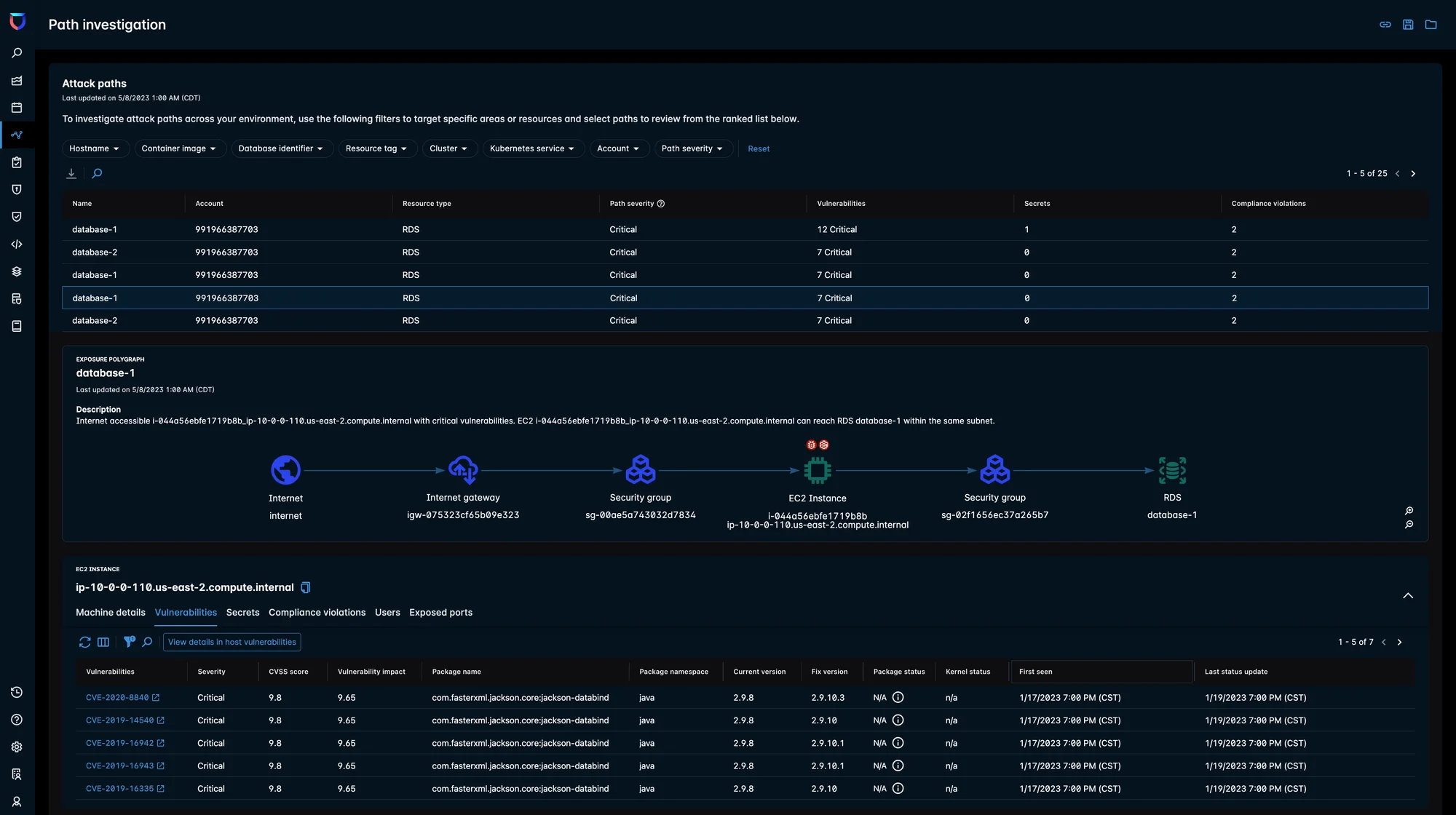
Path investigation
This dashboard enables your security teams to browse through all the potential attack paths and gain more context around specific security concerns. Each attack path has an assigned severity. When determining attack path severity, Lacework takes into account the recently updated host/container vulnerability risk score, which includes internet exposure, active vulnerability detection, and public exploits data. Our platform also considers other risk factors such as misconfigurations, exposed data assets, and secrets to determine the path severity.
With full context about your environment, your teams can now be strategic in implementing effective security controls that precisely minimize security incidents.
Kubernetes coverage
Our platform’s attack path analysis capabilities can now detect risky combinations within different types of Kubernetes service deployments. By ingesting data via a new Kubernetes collector on each cluster, we can provide critical context on where, what, and how vulnerable services are contributing to your attack surface.
Take attack path analysis a step further
The Lacework CNAPP takes attack path analysis even one step further than many modern cloud security vendors. In addition to mapping out attack paths, Lacework shows what’s actively running in the production where these risks can be exploited. This means that when your incident response teams receive an alert that represents a potential breach, they can leverage attack path analysis with runtime data to gain as much context as they can for faster and effective investigation and response.
The attack path analysis and real-time monitoring capabilities from Lacework have been a game changer in proactively mitigating unknown risks and potential attacks. Immediate visibility and context about internet-exposed assets and related risks, such as anomalous logins and publicly reachable assets, has enabled us to prioritize the most critical vulnerabilities, ultimately saving both time and resources.
Prioritize risks and promote trust
Organizations are no longer forced to identify risks such as vulnerabilities, misconfigurations, and internet exposure separately, and then spend hours and resources to build rules, manually correlate the risks, and evaluate the risk posture. With the scale and complexity of the modern cloud environment, your teams need a more efficient and effective way to understand and prioritize your greatest risks. With these new cloud risk management enhancements, your security teams get just that.
But another byproduct of these enhancements? Reinforced trust between security and development teams. With a single source of truth, both security and DevOps can all see the same information from a single place. For example, with a single source of truth, teams can discuss a prioritized vulnerability by looking at the Exposure Polygraph and exploring risk factors.
Similarly, if you detect risky combinations within a Kubernetes service, it is easier to communicate effectively with the developers using a language that they understand. Because, let’s face it, application developers don’t think about their architectures in terms of hosts. They are probably talking about Kubernetes clusters, pods, and services.
Lacework gave us the in-depth risk context we needed to quickly pinpoint potential vulnerabilities and misconfigurations that an attacker could potentially exploit to access our critical data assets. Our security teams can not only focus on fixing the most risky issues with utmost confidence but they can also be more strategic in implementing effective security controls.
Interested in learning more?
Although predicting the future isn’t always possible, our CNAPP provides customers with insight into their most significant risks and potential avenues for security breaches.
Check out this demo video and guided tour to see how attack path analysis can help you reduce your exposure and improve the relationship between security and development teams.
Suggested for you