Why Your Fast Release Cycles are Wasting Precious Developer Time
OverOps
JULY 31, 2020
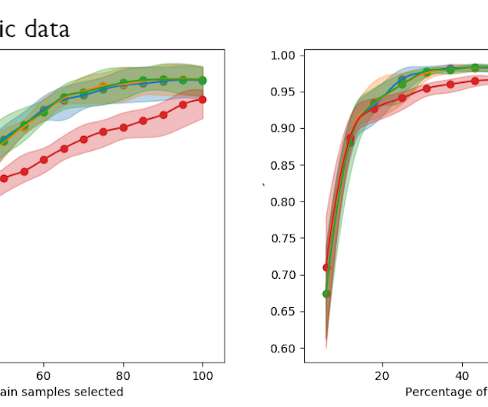
OverOps surveyed over 600 engineering professionals for the 2020 State of Software Quality Report and found that the struggle to balance release speed and quality hurts developer productivity. TL;DR: Download the findings from our 2020 State of Software Quality survey. It used to be said that if you’re not breaking things, you’re not moving fast enough.









































Let's personalize your content