Announcing CN-Series: The Industry’s First NGFW for Kubernetes
Container adoption is on a serious rise, which is why we’re releasing CN-Series, the containerized version of our ML-Powered Next-Generation Firewall (NGFW), designed specifically for Kubernetes environments. It’s a significant development because, according to Gartner, in the next three years, the vast majority of organizations will be running multiple containerized applications in production.
As Unit 42 – the threat research arm of Palo Alto Networks – notes, these growing threats include Graboid: First-Ever Cryptojacking Worm and other new vulnerabilities that could be exploited over the network. For example, our researchers deployed a containerized version of Drupal 8 fully secured by cloud-native security tools in a public cloud. The container was compromised in 45 minutes. You can read more about this particular attack in our whitepaper, “Five Major Security Threats and How to Stop Them.” Incidents like this are just the beginning. As enterprises adopt containers, the number of potential threats to apps running on Kubernetes will only continue to grow.
How Palo Alto Networks addresses critical container security requirements
We believe that complete container security requires the following protections:
- Vulnerability Management – Manage vulnerabilities and prioritize risk at runtime, as well as implement container images scanning and enforcement as part of build and deploy workflows.
- Runtime security – Protect running containers and the host OS by building a baseline of application behavior to alert on and prevent anomalous or unwanted activity.
- Identity-based microsegmentation – Reduce your attack surface by limiting east-west traffic based on the machine and application identity.
- Layer 7 inspection and threat protection – Use full layer-7 network security and threat protection capabilities delivered by NGFWs to protect the allowed connections from threats, exploits, malware and data exfiltration.
Layer 7 NGFW capabilities round out complete container security stack
The release of CN-Series is part of our ongoing commitment to securing cloud applications. We acquired the world's best container security company Twistlock and integrated it into Prisma Cloud to provide shift-left and runtime protection capabilities for hosts, containers and serverless. Then in December of 2019, we acquired Aporeto and are integrating identity-based microsegmentation capabilities into Prisma Cloud as well. And today, we are launching CN-Series, a containerized form factor of our industry-leading NGFW and the industry’s first next-gen firewall for Kubernetes. This ensures our customers have access to a complete container security stack.
As the industry’s first NGFW built specifically for Kubernetes environments, CN-Series firewalls leverage deep container context to protect inbound, outbound and east-west traffic between container trust zones (i.e. between namespaces, or between PCI-infected apps and non-PCI apps), along with other components of enterprise IT environments.
Container connections shouldn’t open infrastructure-wide vulnerabilities
As enterprises speed their adoption of containers, risks also keep growing because containerized applications don't live on an isolated island. As these apps go into production, they start connecting to critical, non-containerized applications such as Active Directory and shared databases still running on legacy systems. This means that if attackers break into a containerized application, they can also break into critical databases by propagating laterally using allowed connections.
As the risk and compliance needs of the container environments increase, network security teams need to secure Kubernetes environments with the same rigor used to protect the rest of the infrastructure. Using familiar approaches won’t work. For example, network security teams may attempt to deploy a traditional NGFW at the edge of a Kubernetes cluster. However, this edge firewall is limited to cluster-level visibility and control – it’s impossible for the edge firewall to identify the specific container pod from which application traffic originates.
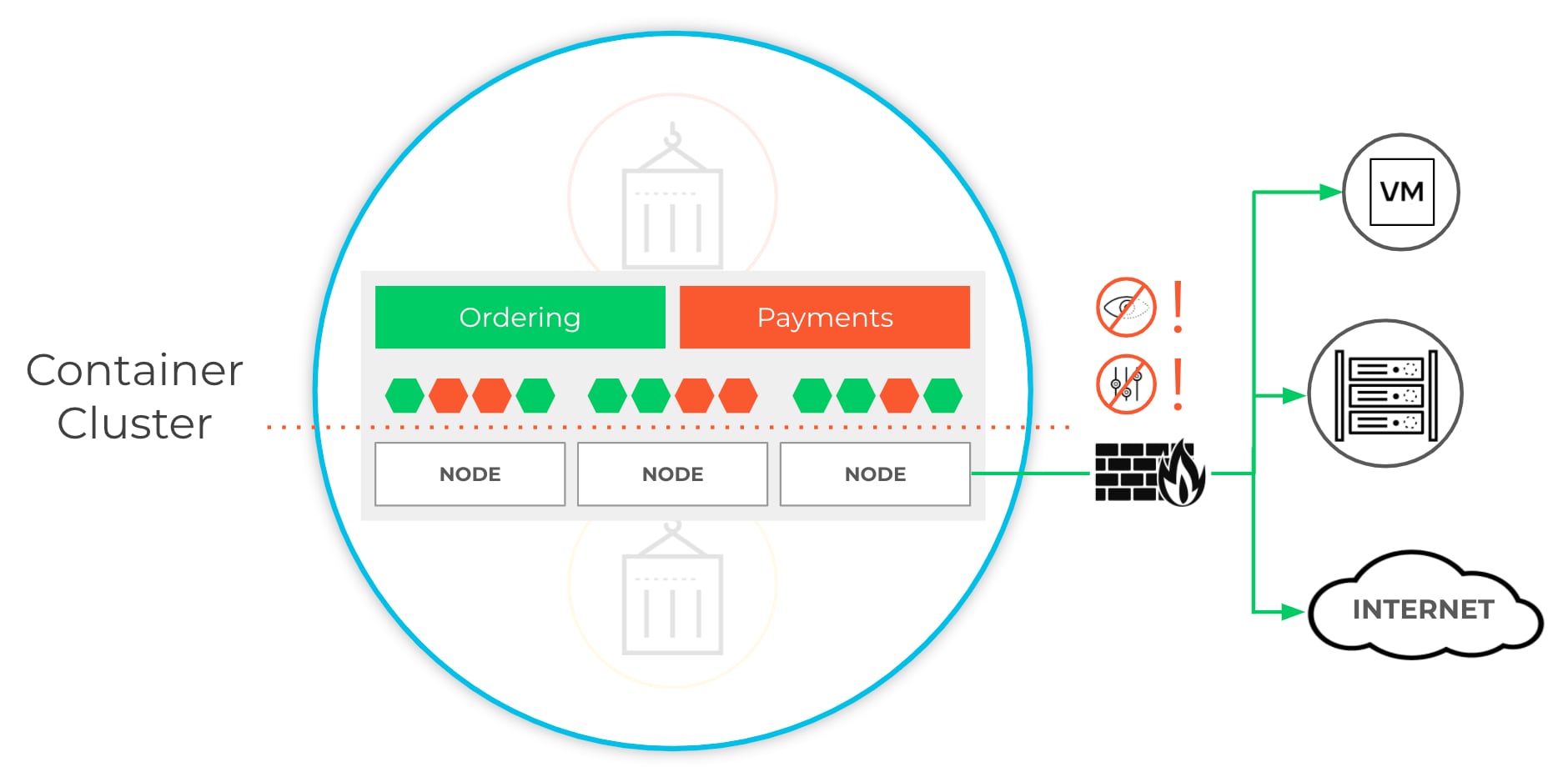
This means that layer-7 network security and threat protection policies cannot be enforced between applications or namespaces within a container cluster. Plus, in a shared cluster, policies must be enforced for the entire cluster or not at all, rather than for specific applications within the cluster. What network security teams really need is an NGFW they can integrate natively into Kubernetes to gain layer-7 visibility for thousands of applications and enforce protection policies more granularly at the application or namespace level within a cluster.
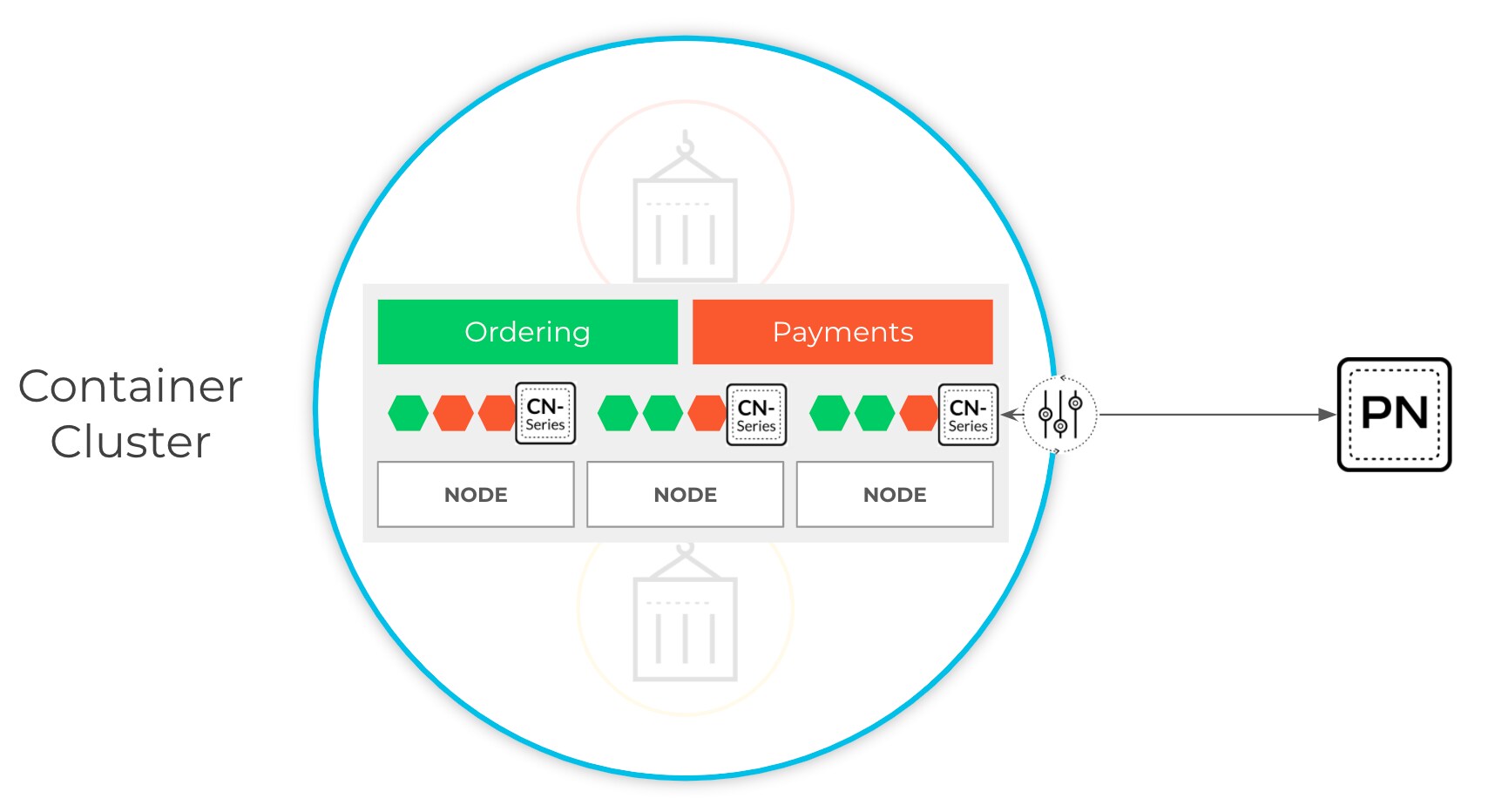
Newfound visibility and protection closes container security gaps
It is for this visibility and protection we have built the CN-Series Container Next-Generation Firewall. By containerizing our industry-leading next-gen firewall, the CN-Series container firewall natively deploys into Kubernetes environments.
Deploying natively allows network security teams to get layer-7 visibility and apply full NGFW protection for all inbound, east-west and outbound traffic at a namespace or even a pod level. CN-Series can be used to protect critical applications against known vulnerabilities and known or unknown malware and threats, until patches can be applied to secure the underlying compute resource. What’s more, URL filtering capabilities can be used to prevent the cloud native applications from connecting to potentially malicious websites or code repositories.
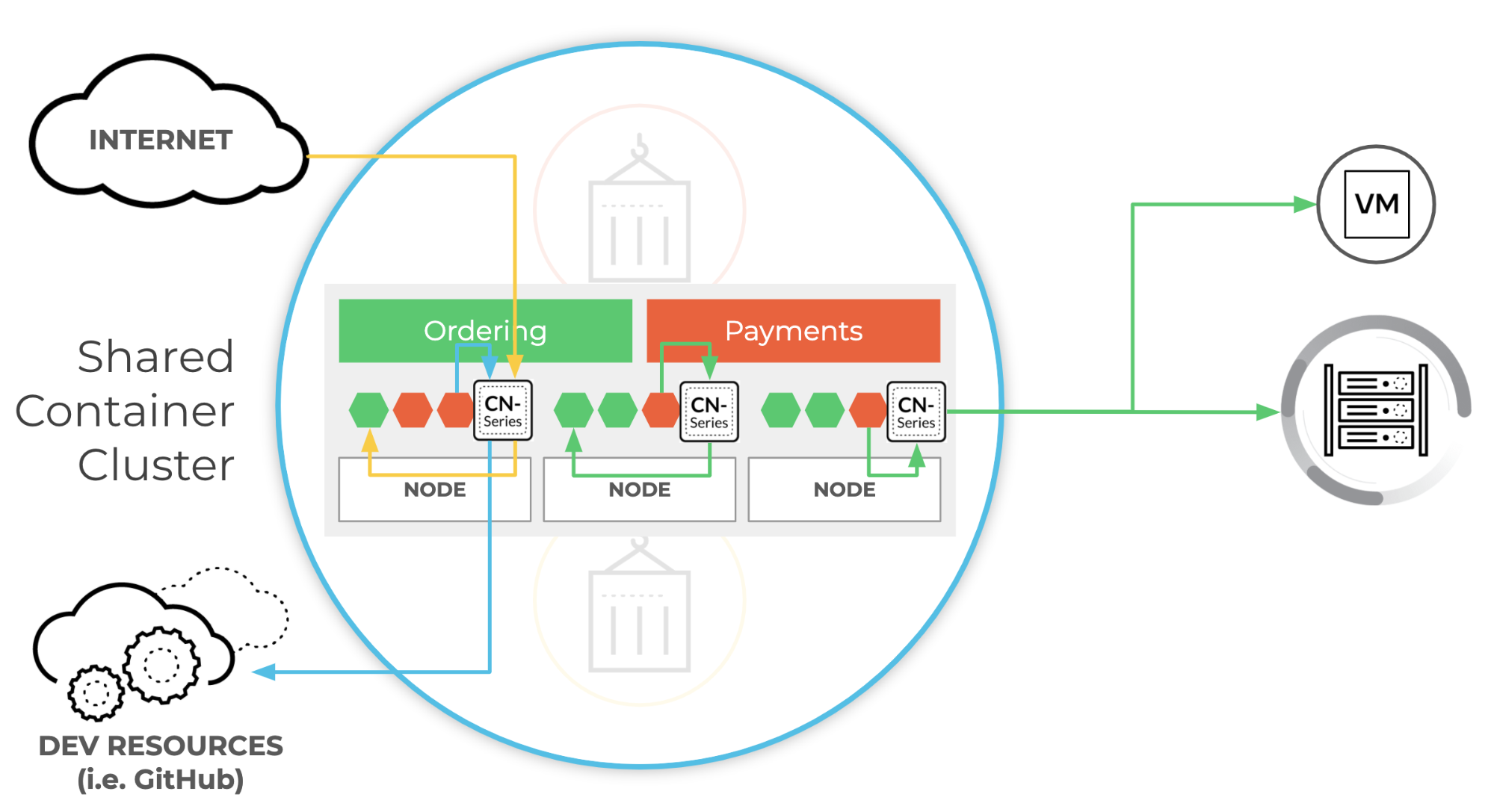
CN-Series can deliver full next-gen firewall protection regardless of where apps are hosted. In an on-prem data center, this can be Kubernetes or Red Hat OpenShift. In a public cloud, this far-reaching protection also includes Kubernetes and Red Hat OpenShift – and is extended to Google Kubernetes Engine (GKE), Azure Kubernetes Service (AKS), and Amazon’s Elastic Kubernetes Service (EKS).
Ease and speed matches need
Because CN-Series deployment and configuration is completely native to Kubernetes, the container firewall can be deployed with simple Kubernetes commands and easily integrated into existing DevOps workflows for fast, repeatable deployments. For development teams that use Helm to manage their Kubernetes applications, a community-supported CN-Series Helm Chart has been created to simplify firewall deployment and management.
And to ensure network security consistency and accuracy throughout the infrastructure, Panorama security management provides centralized administration across physical, virtual and containerized environments. Features such as a brand new Panorama K8s plugin allows customers to enforce context-aware policies in CN-Series as well as in other members of our ML-powered firewall platform: VM-Series virtual firewalls and PA-Series hardware firewalls.
Make container adoption real – and find more details about getting serious about Kubernetes security.
Intelligent Network Security: LinkedIn Live Broadcast.
AJ Shipley, vice president of product, and Paul Calatayud, Americas CSO, appeared on LinkedIn Live to answer questions about the industry’s first ML-Powered NGFW. Watch the event on-demand.
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.