Project Bluefin and the future of operating systems
InfoWorld
APRIL 1, 2024
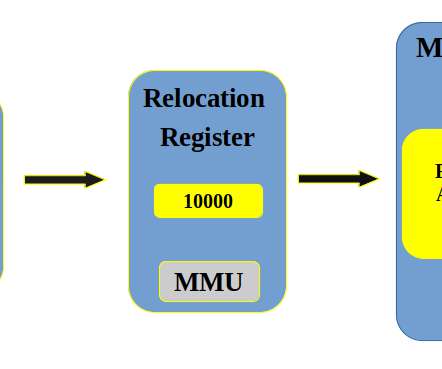
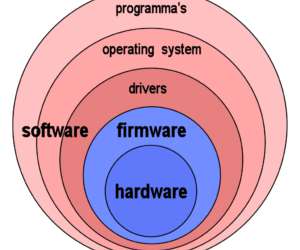
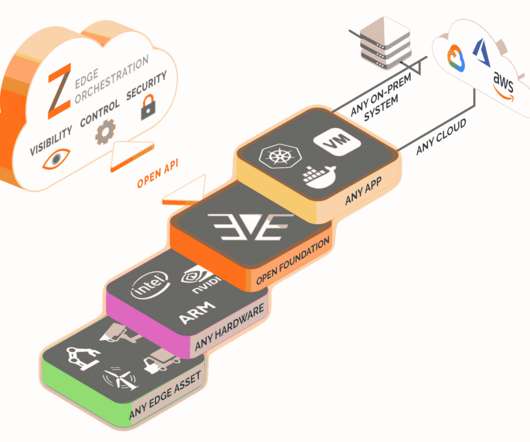
Even with all of the advances in IT, whether it’s modular hardware, massive cloud computing resources, or small-form-factor edge devices, IT still has a scale problem. This means that the basic building block of devops , the operating system, needs to scale—quickly, smoothly, and seamlessly.












































Let's personalize your content