IPv6 Is Finally Ready for Prime Time. Now What?
Symantec
MAY 28, 2019
IPv6 has the potential to make the Internet a safer place. Here’s what you need to know about deploying the new networking protocol
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Symantec
MAY 28, 2019
IPv6 has the potential to make the Internet a safer place. Here’s what you need to know about deploying the new networking protocol
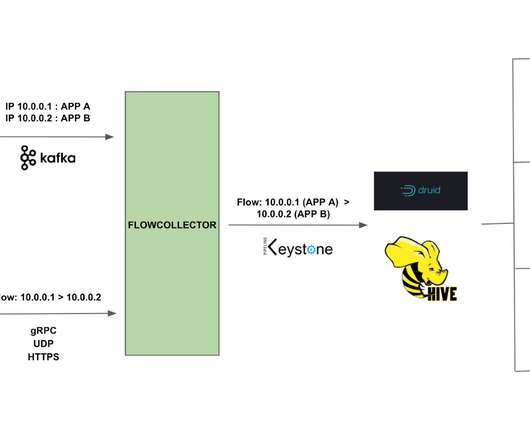
Netflix Tech
JUNE 7, 2021
By Alok Tiagi , Hariharan Ananthakrishnan , Ivan Porto Carrero and Keerti Lakshminarayan Netflix has developed a network observability sidecar called Flow Exporter that uses eBPF tracepoints to capture TCP flows at near real time. Without having network visibility, it’s difficult to improve our reliability, security and capacity posture.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
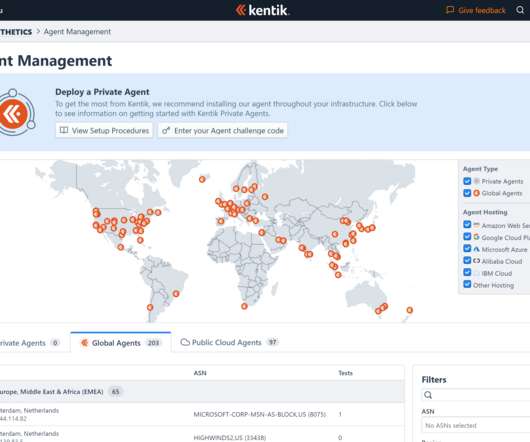
Kentik
AUGUST 28, 2020
We recently launched Kentik Synthetic Monitoring , a major new product feature that combines synthetic network testing with real-time traffic monitoring to provide thorough insight into network performance and reliability. IPv4 raw sockets are able to send the full packet starting with the IP header.

Aqua Security
APRIL 12, 2021
In addition to the deprecation of PodSecurityPolicies , we’ll also look at some newly promoted features being put in place to block Kubernetes vulnerabilities and things like the new IPv6 support which will be one to take account of when designing cluster network security controls.

TechCrunch
FEBRUARY 8, 2022
Jean-Paul Smets is the CEO of Rapid.Space , a hyper open cloud provider offering virtual private servers (VPS), content delivery networks (CDN) and global IPv6 (SDN). Jean-Paul Smets. Contributor. Share on Twitter.

CTOvision
AUGUST 11, 2013
With this post we will dive a bit deeper into bogosity in networks, paying particular attention to the fundamental element of bogosity, the Bogon. We will then articulate a use case for the Centripetal Networks RuleGate which can ensure bogons never get to your enterprise. Filtering private IP addresses requires only a few rules.
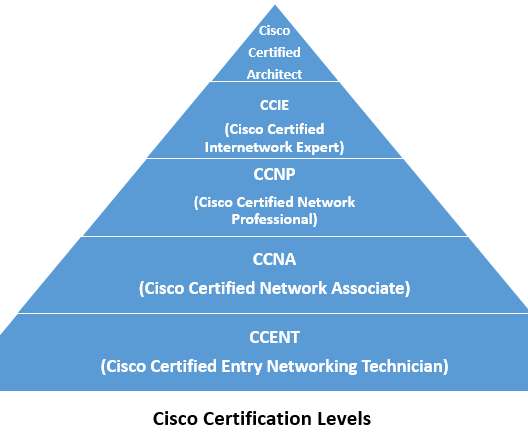
The Crazy Programmer
JUNE 17, 2022
CCNA and CCNP, both are Cisco approved certification courses, which are very popular among those who seek a career in the computer networking line. Cisco is a very reputed and well-settled organization that manufactures and sells network-related equipment and solutions. Cisco Certified Network Associate (CCNA).

DevOps.com
MAY 13, 2020
In addition, the community has added IPv6 support to the Kuryr project for integrating OpenStack with container networking […]. The post OpenStack Delivers Ussuri Update appeared first on DevOps.com.

Tenable
OCTOBER 18, 2022
Accurate and up-to-date accounting of assets residing on federal networks is also critical for CISA to effectively manage cybersecurity for the Federal Civilian Executive Branch (FCEB) enterprise.". This directive applies to all IP-addressable networked assets that can be reached over IPv4 and IPv6 protocols. New requirements.

O'Reilly Media - Ideas
JULY 13, 2021
In networking, we have standards for what data means and how to send it. The fields in the header have been defined precisely, and new protocols have been built successfully at every layer of the network stack. In a network stack, TCP talks to TCP; HTTPS talks to HTTPS. Is data integration a problem that can be solved?
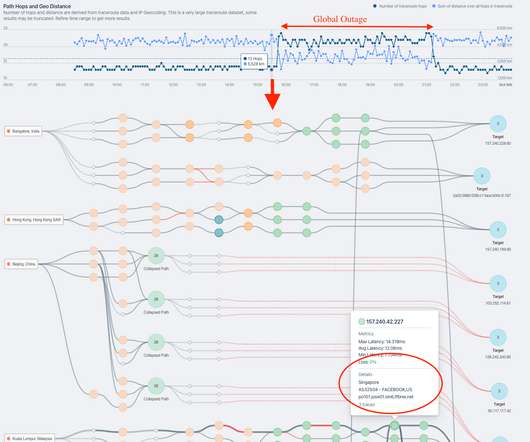
Kentik
OCTOBER 4, 2021
According to a statement published last night, Facebook Engineering wrote, “Configuration changes on the backbone routers that coordinate network traffic between our data centers caused issues that interrupted this communication.” That’s where network observability comes in. See for yourself.

Tenable
DECEMBER 5, 2022
The contest includes a special challenge, a small office/home office (SOHO) “smashup” to simulate a real world attack where an attacker would chain vulnerabilities in multiple devices in order to compromise a home network. A network misconfiguration present in versions prior to V1.0.9.90
Kentik
AUGUST 5, 2021
As the available supply of IPv4 addresses became exhausted and IPv6 adoption lagged, the demand for IPv4 naturally increased. Markets were established and what had once simply been a network configuration setting was now an increasingly valuable virtual commodity.

Kentik
DECEMBER 18, 2017
It’s also just one of the many interesting statistics that we run across as we operate our SaaS platform for network traffic analytics. Network Devices: Which Brands are Trending? Cisco Systems is by far the market leader in the overall IT Networking sector. Google maintains Internet-wide stats on the overall IPv6 adoption rate.

Kentik
DECEMBER 22, 2016
We really respected their thoroughness and the fact that they are practicing network engineers, so as we’ve come up with cool new gizmos in our product, we’ve asked them to extend their review. Following here, from their latest review, are some excerpts that focus on Kentik NPM, our enhanced network performance monitoring solution.

The Crazy Programmer
JUNE 12, 2018
Cisco Certified Network Associate (CCNA) 200-125 exam is designed to test candidate’s understanding and skills in networking basics , LAN and WAN technologies, IPv4 and IPv6 technologies, services, security and management of infrastructure. Attaining a Cisco certification is a gateway to a great career in networking.

CTOvision
NOVEMBER 14, 2016
If IoT devices supporting IPv6 over Low power Wireless Personal Area Networks (6LoWPAN) are introduced, the potential for larger DDoS attacks compounds. These sensors would be deployed in a Machine to Machine (M2M) network, but could utilize 6LoWPAN to connect to the internet.

CTOvision
APRIL 3, 2014
They are: Axon Ghost Sentinel – Hugh Brooks, President, Harrisonburg, VA – Inspired by natural self-organizing systems, Axon Ghost Sentinel’s cyber security products provide lightweight, adaptive, scalable, and decentralized security for mobile and traditional devices, and enterprise networks. CardKill Inc. Fast Orientation, Inc.

Cloudera
JULY 15, 2021
This blog post provides an overview of best practice for the design and deployment of clusters incorporating hardware and operating system configuration, along with guidance for networking and security as well as integration with existing enterprise infrastructure. Networking . IPV6 is not supported and should be disabled.

Kentik
DECEMBER 8, 2016
In networking terms, a “flow” defines a uni-directional set of packets sharing common attributes such as source and destination IP, source and destination ports, IP protocol, and type of service. J-Flow : J-Flow is a flow monitoring implementation from Juniper Networks. What if you don’t have any network devices that can export flow?

Linux Academy
JANUARY 14, 2020
For small or uncomplicated networks, BIND by itself is well suited to provide all DNS-related service functions. Typically, the people who manage BIND DNS servers day to day are network administrators or system administrators who are comfortable in Linux/UNIX. Who Uses BIND? BIND also gives you very granular control over a DNS server.

CTOvision
APRIL 25, 2017
The operator played a critical function in establishing a global telephone network where any phone could talk to any phone. And when you authorize any device to join your home network, your network and your device are smart enough to automatically configure themselves to use your ISP's DNS service.

Zensar
AUGUST 16, 2018
You and your friend visit a noisy club and like everyone, both of you get on the club’s free wifi network. In the world of ‘internet of value’, your application will act as a node which connects to another peer node irrespective of what kind of network you leverage. The post Demystifying ‘Internet of Value’ appeared first on.

High Scalability
OCTOBER 19, 2018
four petabytes : added to Internet Archive per year; 60,000 : patents donated by Microsoft to the Open Invention Network; 30 million : DuckDuckGo daily searches; 5 seconds : Google+ session length; 1 trillion : ARM device goal; $40B : Softbank investment in 5G; 30 : Happy Birthday IRC!; They'll love it and you'll be their hero forever.

Linux Academy
FEBRUARY 11, 2019
IPv6 is another major addition to the platform, reflecting the next generation of networking. You’re able to set a master node with child nodes to see how they interact, and you’re able to configure container networking between different servers, to name a few examples. Upgraded interface and server logs.

High Scalability
JUNE 22, 2018
40 million : Netflix monthly spend on cloud services; 5% : retention increase can increase profits 25%; 50+% : Facebook's IPv6 traffic from the U.S, Setting aside the network quality & performance, which is objectively superior with Google, outside of GCE almost every other GCP product is offered as a managed service.

CableLabs
MAY 20, 2021
P4”-based) and uses in-band network telemetry (INT) technology for device identification and mitigation, blocking attack traffic where it originates on the operator’s network. These factors contribute to a trend of malicious traffic increasingly using upstream bandwidth on the access network.

AlienVault
OCTOBER 29, 2018
Sogou.exe is the payload that contains the CPUInfo scanner, however, it has been set to scan for IPV6 addresses. In addition, in Sogou.exe, MadoMiner appears to search for IPV6 addresses that are vulnerable to EternalBlue, as well as installs some tasks. Sogou is saved as Conhost.exe in C:WindowsInstaller.
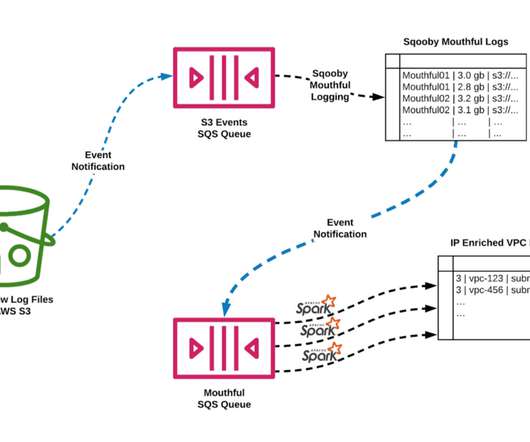
Netflix Tech
MAY 26, 2020
Without having network visibility, it’s not possible to improve our reliability, security and capacity posture. Network Availability: The expected continued growth of our ecosystem makes it difficult to understand our network bottlenecks and potential limits we may be reaching. 43416 5001 52.213.180.42 43416 5001 52.213.180.42

Apps Associates
JUNE 22, 2022
M6id instances also provide customers up to 50 Gbps of networking speed and 40 Gbps of bandwidth to Amazon Elastic Block Store , twice that of comparable previous generation instances. Customers moving to IPv6 can simplify their network stack by running their databases on a network that supports both IPv4 and IPv6.

Xebia
AUGUST 29, 2023
Transit VPCs are a specific hub-and-spoke network topology that attempts to make VPC peering more scalable. However, this requires a self-managed network router in the Transit VPC and you need to take great care to avoid overlapping CIDR ranges across VPCs. At the highest level, VPC Lattice distinguishes Services and Service Networks.

ParkMyCloud
OCTOBER 6, 2020
IP addresses will be either an IPv4 or IPv6 address. While you can give your instance multiple private IPv4 and IPv6 IP addresses, it’s important to note that the number of interfaces and private IP addresses you can specify for an instance depends on the instance type. This is a virtual network that is dedicated to your AWS account.
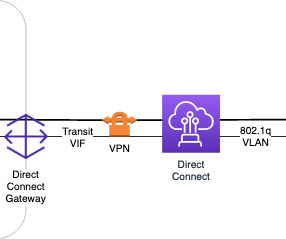
Perficient
MAY 11, 2023
Agenda Autonomous System and BGP what is Site-to-Site VPN Flow Diagram and Architecture Site-to-Site VPN features Site-to-Site VPN limitations Customer gateway and Virtual Gateway Limitation Alternate VPN Demo What is Autonomous System: The Internet is a network of networks, and autonomous systems are the big networks that make up the Internet.
O'Reilly Media - Ideas
SEPTEMBER 5, 2023
Security Proof-of-work makes it to the Tor network. Among other things, this change is intended to accelerate IPv6 adoption. It has a museum… And Flash games will run in a modern browser using Ruffle , a Flash Player emulator that is written in WebAssembly. It is used as a defense against denial of service attacks.

Kentik
FEBRUARY 8, 2016
For reasons of enforced obfuscation by RFC writers, routes are also called Network Layer Reachability Information (NLRI). As of December 2015, there are over 580,000 IPv4 routes and nearly 26,000 IPv6 routes. Another foundational concept is the Autonomous System (AS), which is a way of referring to a network.

Aviatrix
OCTOBER 16, 2018
Amazon Virtual Private Cloud (Amazon VPC) lets you provision a logically isolated section of the AWS Cloud where you can launch AWS resources in a virtual network that you define. You can use both IPv4 and IPv6 in your VPC for secure and easy access to resources and applications.

Kentik
MARCH 28, 2016
How flow protocols adapt as network needs evolve. Network flow records today are an integral part of the network operations landscape. What about capturing MAC address, or VLAN tag, or IPv6? IPv6, MAC addresses, VLAN, and MPLS) makes it more limited than other alternatives.

Kentik
DECEMBER 18, 2019
When it comes to analyzing network traffic for tasks like peering, capacity planning, and DDoS attack detection, there are multiple auxiliary sources that can be utilized to supplement flow information. IPv6 peerings are starting to outgrow a single node. It also allowed mirroring the setup for our IPv6 fabric.

Tenable
JANUARY 26, 2023
Record types : It’s useful to know, for example, that a record type is an A record vs an AAAA record because the reason one user can see the content and another can’t see it might have everything to do with the fact that they aren’t able to connect to IPv6 from their house, while another user can.

Kentik
AUGUST 21, 2017
No matter how well your network is routing IP traffic, the network is essentially down without DNS to resolve hostnames like www.google.com to their underlying IP addresses. As with any critical component, network operations needs to be able to continuously monitor DNS performance and to respond quickly to any issues that may arise.

Kentik
APRIL 18, 2016
Also, to cut down on CPU and network bandwidth, flows are usually only “exported” on average every 10 seconds to a few minutes. sFlow, on the other hand, is based on interface counters and flow samples created by the network management software of each router or switch. This can result in very bursty traffic on sub-minute time scales.
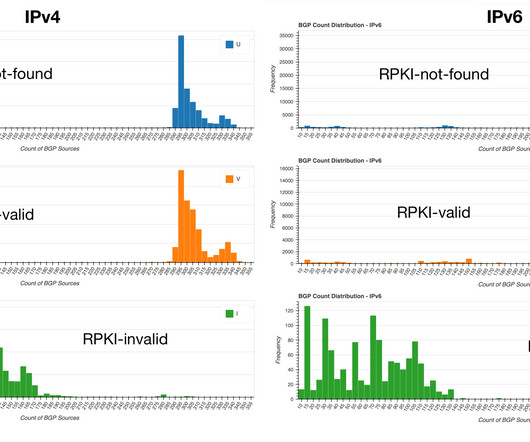
Kentik
MAY 23, 2023
Since our analysis last year, the number of ROAs has climbed continuously and, at the time of this writing, stands at 43.17% for IPv4 and 45.17% for IPv6. So in the past year, the share of BGP routes (IPv4 and IPv6) evaluated as RPKI-valid increased by roughly a third! as well as large access networks (Comcast, Spectrum, etc.).

taos
OCTOBER 8, 2019
Non-Optimized Performance Without specific performance optimizations for high-bandwidth long-haul networks, TCP throughput is a function of network latency. Window Scaling IETF RFC 1323 defines TCP window scaling, as an optional feature to improve performance over “Long, Fat Networks”. Optimizing Performance?—?Window
Expert insights. Personalized for you.
Are you sure you want to cancel your subscriptions?


Let's personalize your content