Fighting Ransomware: Using Ivanti’s Platform to Build a Resilient Zero Trust Security Defense
Ransomware is a strain of malware that blocks users (or a company) from accessing their personal data or apps on infected iOS, iPadOS, and Android mobile devices, macOS laptops, Windows personal computers and servers, and Linux servers. Then the exploit demands cryptocurrency as payment to unblock the locked or encrypted data and apps. This form of cyber extortion has been increasing in frequency and ferocity over the past several years. Seemingly, a week does not pass without hearing about the latest ransomware exploit attacking government agencies, healthcare providers (including COVID-19 researchers), schools and universities, critical infrastructure, and consumer product supply chains.
The most common delivery mechanisms are email and text messages that contain a phishing link to a malicious website. By tapping on the link, the user is redirected to an infected website where they unknowingly download drive-by malware onto their device. The malware can contain an exploit kit that automatically executes malicious programmatic code that performs a privilege escalation to the system root device level, where it will grab credentials and attempt to discover unprotected network nodes to infect via lateral movement.
Another common delivery mechanism are email attachments that can also contain malware exploit kits that affix themselves to vulnerable apps, computer systems or networks to elevate their privileges in search of critical data to block.
There are 4 main types of ransomware. First is the locker ransomware, where the earliest form on mobile devices was found on Android. It was detected in late 2013 and called LockDroid. It secretly changed the PIN or password to the user’s lock screen, preventing access to the home screen and to their data and apps.
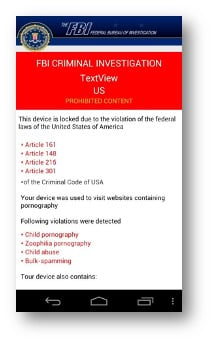
The second type are encryptor ransomware that employs encryption of apps and files making them inaccessible without a decryption key. The first exploit using this type of ransomware was found in 2014 and called SimpLocker. It encrypted the personal data contained within the internal Secure Digital (SD) storage of an Android device. Afterward, an official looking message showing criminal violations based on scanned files found in the device is displayed to the victim. This is followed by a demand for payment message that would allow the victim to resolve the fake violations and receive the decryption key to unlock their blocked data and apps.
Extortion payments are often made with Monero cryptocurrency because it is digital and often untraceable, ensuring anonymity for the cybercriminals. Bitcoin is still sometimes used, but lately, companies like CipherBlade have been able to track down ransomware gangs using Bitcoin and return the money back to victims. Rarely, mobile payment methods like Apple Pay, Google Pay or Samsung Pay are also used, but cryptocurrency is still the preferred payment for ransomware.
Just within the past several years, cybercriminal gangs have added several more types of ransomware exploits including Doxware, which are threats to reveal and publish personal (or confidential company) information onto the public internet unless the ransom is paid. The other is Ransomware-as-a-Service (RaaS). Cybercriminals leverage already developed and highly successful ransomware tools in a RaaS subscription model, selling to lesser skilled cybercriminals to extort cryptocurrency from their victims and then share the ransom money.
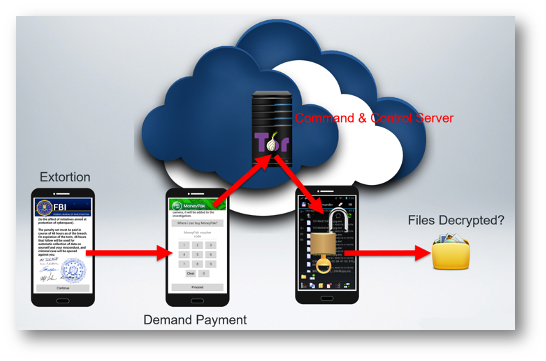
Android Exploits: Anatomy of the SimpLocker Attack
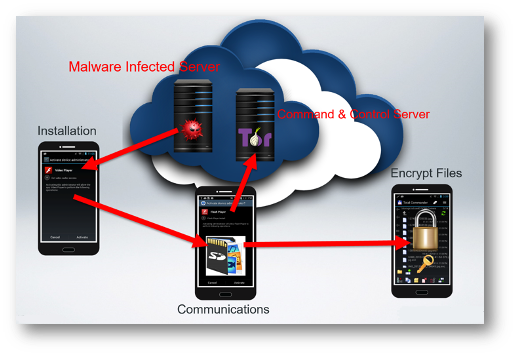
Installation: The victim unknowingly lands on malware compromised or Angler hosted web server and wants to play a video or run an app. The video or app requires a new codec or Adobe Flash Player update. The victim downloads the malicious update software and installs it, requiring device administrator permissions to be activated. The mobile device is infected, and the ransomware payload installs itself onto the device.
Communications: The malware scans the contents of the SD card. Then it establishes a secure communications channel with the command and control (C2) server using the anonymous Tor or I2P proxy networks within the darknet. These networks often evade security researchers, law enforcement, and government agencies making it extremely difficult to shut them down.
Encrypt Data: The symmetric key used to encrypt the personal data on the attached SD card are kept hidden within the infected mobile device’s file system so the encryption can persist after reboots.
Extortion: An official looking message from the FBI, Department of Homeland Security, or other government agency is displayed informing the victim that they are in violation of federal laws based on data found on the device after a scan of their personal files.
Demand Payment: A demand-for-payment screen with instructions on the method of payment is then displayed. The fine was normally $300 to $500 and commonly paid in cryptocurrency.
If the ransom payment is made, the symmetric key is provided and used to decrypt the personal data. If the victim is fortunate, they can retrieve all their personal files intact, although there have been reports that some if not all the data are corrupted and no longer usable after they are decrypted.
Android devices are especially susceptible to ransomware because of several factors. First is its global adoption with 72% of the worldwide market share and 3 billion devices around the world. Next is the 1,300+ original equipment manufacturers (OEM), along with the fragmentation of the Android operating system. Devices running versions from 2.2 to 11.0, means a very large number of them never receive a critical security update leaving them vulnerable to malware.
The last factor is Android users routinely root their devices and install apps that are unverified by Google. There are now an estimated three million apps available for download just from the Google Play Store, with potentially a million more that can be downloaded from unknown and many malicious sources. Any one of these apps can be used to host malware that can lead to ransomware exploits.
Android Remediation
Here are the remediation tasks to help fight ransomware on Android devices.
These settings are configured within the Android device: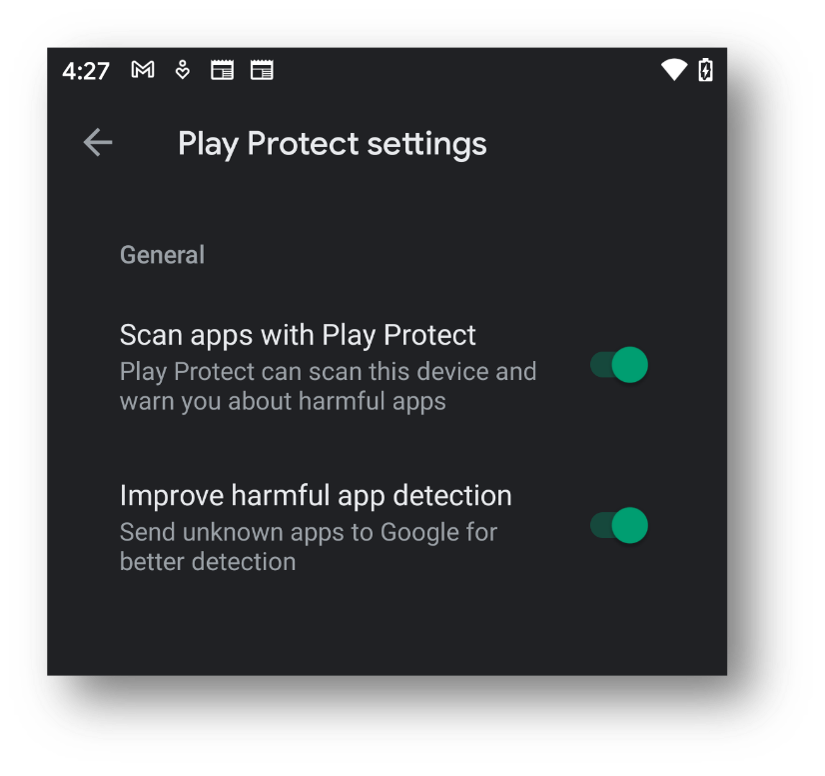
1. By default, within the Google Settings and Security configuration, the Google Play Protect settings Scan apps with Play Protect and Improve harmful app detection are enabled. These settings are the equivalent to a resident antimalware agent on the device and should remain enabled.
2. Within the Apps & notification and Special app access configuration is Install unknown app settings. Leave storage, email and browser apps as Not allowed, which is the default setting.
These settings are configured within Ivanti UEM for Mobile or MobileIron Core:
3. For Android Enterprise devices, the above settings can be configured using the Lockdown & Kiosk configuration. Select Enable Verify Apps and Disallow unknown sources on Device or Disallow Modify Accounts.
4. Create a System Update configuration to automatically update to the latest available Android OS version for the device. Ivanti Mobile Threat Defense (MTD) can also enforce that the latest OS version is running on the Android device and if not, alert the user and UEM administrator that the device is running a vulnerable OS version and apply compliance actions like block or quarantine until the device is updated.
5. Enable Ivanti MTD on-device (using MTD Local Actions) and cloud-based to provide multiple layers of protection for phishing (Anti-phishing Protection) and device, network and app level threats (using the Threat Response Matrix within the MTD management console).
6. Create a SafetyNet Attestation configuration that checks for device integrity and health every 24 hours via Google APIs.
7. Create an Advanced Android Passcode and Lock Screen configuration to turn on multi-factor authentication (MFA) for the lock screen and work profile challenge using a biometric fingerprint, face unlock, or iris (eye) scan instead of a passcode or PIN.
8. Enable Device Encryption. This may sound counter-intuitive but encrypting your personal and work data on the device can prevent the cybercriminals from threatening to publish your work or company information online.
 9. Backup data automatically onto a cloud storage provider like Google Drive, OneDrive, Box or Dropbox. Make secondary and tertiary copies of backups using two or more of these personal storage providers since some offer free storage. Also, backup personal data onto a local hard drive that is encrypted, password-protected and disconnected from the device and network.
9. Backup data automatically onto a cloud storage provider like Google Drive, OneDrive, Box or Dropbox. Make secondary and tertiary copies of backups using two or more of these personal storage providers since some offer free storage. Also, backup personal data onto a local hard drive that is encrypted, password-protected and disconnected from the device and network.
10. Enable Android Enterprise or Samsung KNOX on the device to containerize, encrypt, and isolate the work profile data from your personal data in BYOD or COPE deployments. Android Enterprise in the various deployment modes and Samsung KNOX can be provisioned by Ivanti UEM for Mobile or MobileIron Core.
11. For BYOD deployments, create a blacklist of disallowed apps on the device. For company-owned devices, create a whitelist of allowed apps that can be installed on the device. Both settings can be configured within MobileIron Core’s App Control feature and applied to the security policy. For Android Enterprise devices, Restricted Apps and Allowed Apps can be applied to the Lockdown & Kiosk configuration or Create an App Control configuration to whitelist or blacklist apps within the personal profile side of the device. This can also be configured within Ivanti UEM for Mobile’s Allowed App settings and Policies & Compliance.
12. Configure a VPN client on the device like MobileIron Tunnel, Ivanti Secure Connect or Zero Trust Access to protect sensitive data-in-motion between the mobile device and MobileIron Sentry or Connect Secure or ZTA gateways.
13. Enable Ivanti Zero Sign-On (ZSO) for conditional access rules like trusted user, trusted device, and trusted app authentication to critical work resources on-premises, at the data center, or up in the cloud. Also, enable MFA using the stronger inherence (biometrics) and possession (device-as-identity or security key) authentication factors. Passwords and PINs can be phished, guessed or brute forced.
14. As a last resort, there are anti-malware vendors that provide software to detect and remove ransomware from an infected device. The user can also boot the device into Safe Mode, deactivate the Device Administrator for the malware, and then uninstall it.
In the next blog in this series, we will discuss ransomware attacks and remediation on iOS and iPadOS mobile devices, and macOS laptops and desktops.

