No Policies. No Rules. No Logs.
It’s the brass ring of security professionals everywhere: spot every breach in less than one day. Can it be done?
On average, how many days does it take to detect a security breach in a modern hybrid cloud environment? 205 days? 146 days? 99 days? The truth is, it doesn’t matter. Any security breach that’s not caught on day zero can lead to disastrous consequences. By the numbers, it’s clear there’s still much work to be done:
- Since 2015, the time it takes to discover and remediate a breach has dropped from 205 days to 99 days¹. Sounds good, right? Unfortunately, Mandiant thinks this drop may not reflect improving security — it may simply reflect the rise in bolder attacks, like cyber ransom². By design, those attacks are detected immediately.
- Shockingly, some 25% of enterprises don’t know whether or not they’ve been breached³. I guess that’s a dwell time of, well, infinity.
- 48 of 50 states have security breach notification laws on the books⁴. It makes me wonder what’s going on with the other two…
Today’s security professionals are inundated with every kind of tool. Almost all of them depend on policies, rules and log analysis. None of them provide the time to value and easy implementation people expect from today’s hybrid cloud. Breach detections take forever. Investigations are incredibly complicated. Closing out an investigation — and showing management that you’ve fixed the vulnerability — is a nightmare.
So, after decades of endlessly rolling the security rock up a never-ending hill, why am I optimistic? Why do I think we stand on the threshold of gaining the upper hand against attackers? After all, the tools on the market don’t seem to have made much of a dent, and it’s certainly no easier to predict a hacker’s mindset or forecast the next big exploit.
The fact is every datacenter, every workload, every container, every application has its own truth. That’s always been the case. What’s different now is our ability to use that truth to instantly spot attacks and breaches. Baselining a cloud service, and then using that baseline to spot attacks in progress, has always been a good idea. But baselining gets really complex, really fast. That’s the problem we decided to tackle, and that’s the problem we were inspired to solve.
For two years, a dozen security and analytics experts in Mountain View, California have worked to build a solution that captures the truth behind every cloud workload without the hassle of policies, rules, and logs. Our company is called Lacework and we are about to introduce Polygraph, the industry’s first zero-touch cloud security platform. I could not be more proud of my team and the contributions Lacework is about to make to the security market.
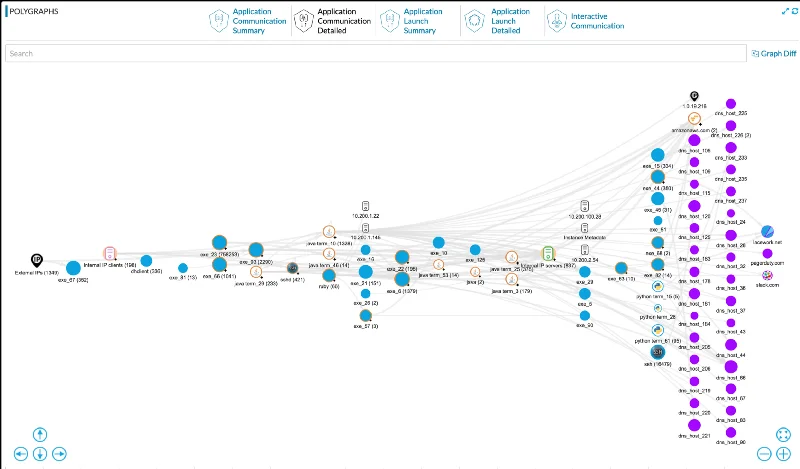
Polygraph’s Deep Temporal Baseline tells the story of every breach — when it happened, how it worked, and what was hit — so you can stop it, fix it, and move on. By spotting deviations from normal operations, we deliver immediate insights into the cyber kill chain so you can understand and remediate cyberattacks and insider threats. Once installed, Polygraph automatically sets to work. Customers start seeing results within hours — the time to value is truly unprecedented and our new GUI invites exploration and discovery. Here’s a screenshot showing the entities and relationships of a typical cloud workload:
Lacework is part of the Sutter Hill Ventures portfolio, along with other visionary cloud companies like Pure Storage, Snowflake and Wavefront. We’re coming out of stealth next week, and we intend to grab the brass ring: we’ll drive the mean exploit detection time to less than a day. And we’ll deliver the precise and timely investigative tools that our customers need to permanently and definitively remediate vulnerabilities.
Starting this week Polygraph is available on the AWS marketplace, with hourly subscription pricing designed to dovetail with the AWS pricing model. Next week our doors will open to serve the DevSecOps and CISO community globally from our new office in Mountain View, where it all began 2 years ago.
References:
2 Mandiant M-Trends, p. 7
Categories
Suggested for you