Azure-Specific Policies to Detect Suspicious Operations in the Cloud Environment
Prisma Clud
APRIL 20, 2023
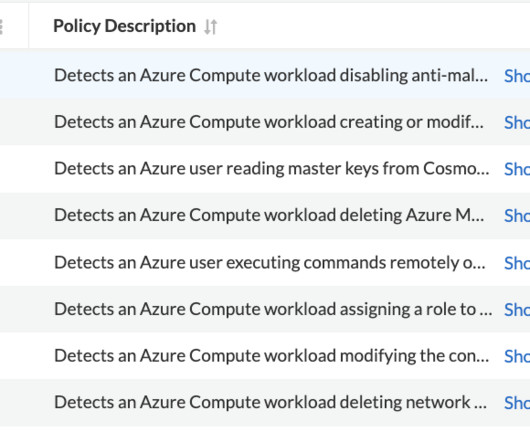
The timely detection and containment of security threats rely on anomaly policies that issue high-fidelity alerts for suspicious operations — and free security teams to investigate and remediate critical incidents. Based on policy results, security alerts are triggered, with operations detected having a high fidelity for malicious activity.



































Let's personalize your content