2 Innovations That Can Tip the Balance in Cybersecurity
CIO
JANUARY 13, 2023
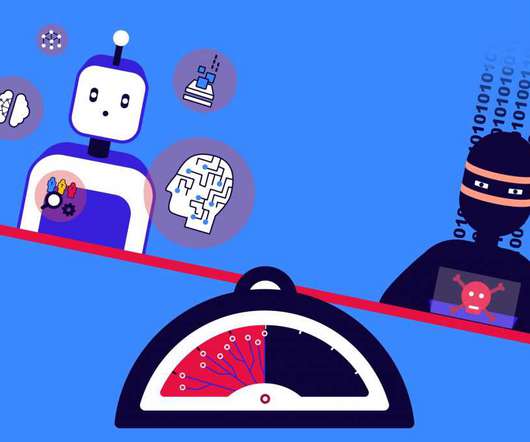
Army Major General and Vice President and Federal Chief Security Officer for Palo Alto Networks What critical innovations can change the balance in cybersecurity, providing those of us responsible for defending our organizations with more capabilities against those who would do us harm? This is not just a theoretical exercise.

















































Let's personalize your content