Survey: More Cybersecurity Pros Embedded in DevOps Teams
DevOps.com
MARCH 7, 2023
A survey of 2,500 C-level executives published today by Palo Alto Networks found 81% of organizations have embedded cybersecurity professionals within their DevOps teams. Despite the presence of those cybersecurity professionals, however, the survey also suggested there is much work to do in terms of optimizing DevSecOps workflows.












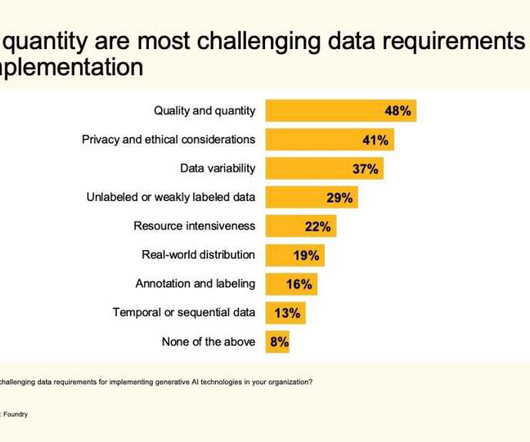






































Let's personalize your content