To paraphrase the protagonist of the aforementioned novel:
There's a scarlet thread of security holes running through the colorless cloud of digital life, and our duty is to unravel it, isolate it, and expose every inch of it.
For the past six years, Security Innovation has been honored to have our award-winning CMD+CTRL Basecamp cyber ranges featured as a CTF (capture the flag) challenge at DEFCON, one of the world's most attended security conferences. Building upon the demand for cloud security skills, this year, we treated players to our latest and most innovative cyber range yet: MailJay – a SaaS solution built on a cloud-native tech stack.
Comprising 46 vulnerabilities, MailJay reflects the risks of modern cloud environments: misconfigurations, access control problems, container issues, and insecure code. Like the previous two cyber ranges featured at DEFCON, MailJay's cloud-centric challenges are mapped to the MITRE ATT&CK Framework.
We've learned first-hand (in our own services work and running cloud CTFs at DEFCON for the past three years) that for organizations to secure their enterprise, they need to upskill their IT professionals in designing cloud solutions, coding for the cloud, and configuring cloud infrastructures. Any one in isolation is simply not enough.
This year, with nearly 100 players, we had folks self-select their job functions from the NICE work roles (with a few opting out of choosing one). We then grouped participants into Builders, Operators, and Defenders to analyze their performance. What we found supports the industry's shift in mentality that:
- Secure software is not just about secure code – but secure design and configuration
- Security is not just the job of the security teams, especially in cloud-dependent organizations
- A defense in depth strategy is critical to making it harder for attackers to achieve success
Securing code reduces only a fraction of software risk
This shift away from just secure coding is seen in many standards. In recent years, the OWASP Software Assurance Maturity Model (SAMM) has expanded the business functions beyond Construction, Implementation, and Verification to include Governance and Operations.
Most code in a modern business application isn't developed from scratch; it is borrowed, bought, or adapted from open-source, COTS, 3rd-party libraries, and the like. As a result, a Dev team's ability to understand and secure that code is limited – sometimes by license restrictions; other times by the simple fact that someone else wrote it, documented it, and (in some cases) left in a lot of extraneous bloat that gets inherited as technical debt (including security vulnerabilities).
To reflect this current reality, we built MailJay with both code and ecosystem-level vulnerabilities. Just like in real-world production, securing the code you have access to in MailJay doesn't secure the application as a whole. It's still possible to exploit cloud misconfigurations, design flaws, and weak access controls to extract data, expand your privileges, discover public S3 buckets, and destroy critical systems.
This trifecta focus on defense in depth, distributed security responsibility, and going beyond secure code was the focus of our DEFCON 30 CTF Village experience… and I dare say it was a rousing success. Indeed, the game is afoot!
Security knowledge no longer hoarded by security teams
Our global economy is increasingly digital. The race to adopt cloud services, DevOps, and uber-connected devices have made every company a software company. An extension of this reality is that security is not just the job of the InfoSec team anymore – job functions from this year's participants included Software Development, Engineering, DevOps, Systems Architecture & Administration, and Vulnerability & Threat Assessment. An interesting trend is how quickly the Operations teams are gaining security skills. In past years, the Defenders (think in terms of job titles like Penetration Testing or Vulnerability Assessment & Management) scored significantly higher than their Dev and Ops teams counterparts. This year, Ops closed the gap (a lot)!
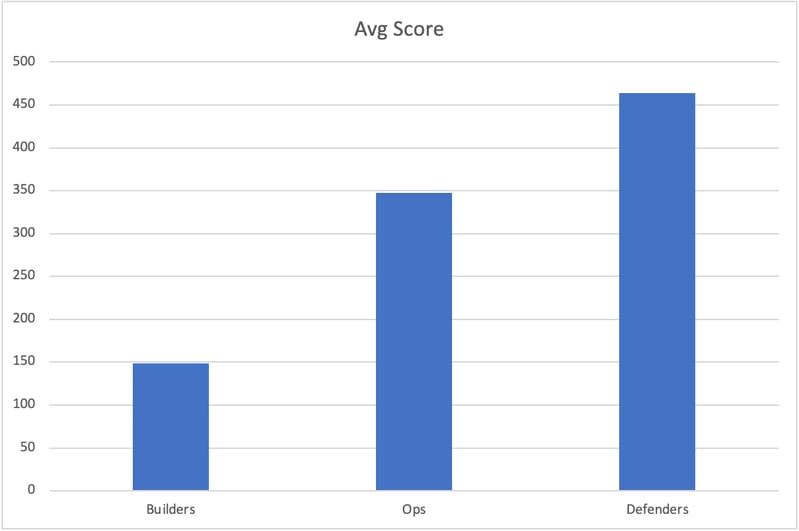
Unsurprisingly, Defenders scored 3x as many points as builders, on average; however, they only outscored those who identified as Operations by 33%. Ops is catching up… and it's the cloud forcing their hand.
As organizations migrate from a data center model to a cloud-centric model (native, hybrid, et al), the 24x7 access from anywhere nature of business has made the issue of reconnaissance a virtually moot point. Initial discovery is simple. Also, the (arguably over-) spending on trying to prevent initial access should continue to wane. That is not an enterprise’s biggest threat.
Defense in Depth works!
MITRE ATT&CK® is ideal for taking a defense in depth approach because it reflects the various phases of an adversary's attack lifecycle. It's based on real-world observations and includes 14 categories and 200+ techniques:
| 1: Casing The Joint | 2: Entering Unlawfully | 3: Maximizing Damage |
| • Reconnaissance: gathering information to plan operation | • Execution: running code on a local or remote system |
• Discovery: understanding what can be controlled |
| • Resource Development: establishing resources to support operations | • Persistence: maintaining a foothold |
• Lateral Movement: moving through the environment |
| • Initial Access: gaining initial foothold |
• Privilege Escalation: gaining higher-level permissions | • Collection: gathering info to achieve ultimate goal |
| • Defense Evasion: avoiding detection | • Command and Control: controlling systems | |
| • Credential Access: gaining legitimate credentials | • Exfiltration: stealing data |
|
| • Impact: compromising integrity |
One should assume that initial access is possible and focus resources on preventing lateral movement, escalation of privilege, exfiltration, and command & control access. We stuffed MailJay full of such challenges (the more damaging ones), so teams can learn the current threats of modern tech stacks – IT systems rife with cloud services, native-cloud development, and software-controlled systems.
The last two DEFCONs (28 and 29) showed us that the early-stage ATT&CK techniques are easier for most people to tackle, e.g., gaining initial access and maintaining persistence inside the target system versus lateral movement and exfiltration of data. This year the cyber range challenges were more complex. As a result, the earliest (left-most) ATT&CK techniques were the most commonly solved: reconnaissance and resource development. Initial access to the system and credentials dropped way down. This is also reflective of the native-cloud development and deployment environment of MailJay. The tech stacks are newer than previous CTF platforms; therefore, the attacks are less well known (not as pervasive) in the groups chartered with building, operating, and protecting those same new cloud-heavy tech stacks.
| MITRE ATT&CK Technique | DEFCON 28 Forescient |
DEFCON 29 Infinicrate | DEFCON 30 MailJay | |
| Casing the Joint | Reconnaissance | 38% | ||
| Resource Development | 36% | |||
| Initial Access | 74% | 55% | 10% | |
| Unlawful Entry | Persistence | 55% | 40% | 8% |
| Privileged Escalation | 6% | |||
| Defense Evasion | 14% | 10% | 16% | |
| Credential Access | 52% | 38% | 9% | |
| Damage & Loss | Discovery | 60% | 24% | 9% |
| Lateral Movement | 4% | |||
| Collection | 61% | 31% | 5% | |
| Command & Control | 9% | |||
| Exfiltration | 29% |
6% |
||
| Impact | 26% | 17% | 6% |
Cyber Ranges:
Forescient: AWS Infrastructure with front-end website, virtual servers, accounts, and more.
Infinicrate: Cloud File store application for teams using GitHub, cloud services, and development tools.
MailJay: Insecure email marketing platform built on a cloud-native tech stack.
You can also see how our cyber ranges (and the industry) have shifted from "can you get in?" to focusing on what one can achieve post-access. This is precisely why organizations must take a defense in-depth approach to secure cloud operations. Don't just think of keeping them out – think about making it more challenging at each phase of an attack, techniques to mitigate success and impact through solid data protection, monitoring, and alerting.
About Lisa Parcella, Vice President of Product Management
With a background in security awareness, product management, marketing communications, and academia, Lisa leverages her vast experience to design and deliver comprehensive security-focused products and educational solutions for the company’s diverse client base. Before joining Security Innovation, Lisa served as Vice President of Educational Services at Safelight Security. She holds a B.A. from the University of Vermont and an M.A. from Boston College. Connect with her on LinkedIn.


