SASE success: Avoid confusion and embrace a single-vendor solution
CIO
NOVEMBER 2, 2023
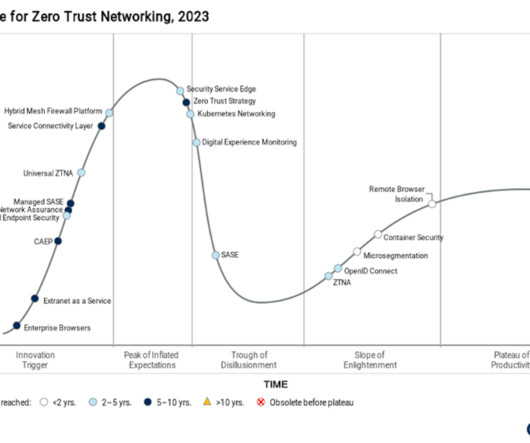
There are vendors that over-promise and under-deliver with SASE solutions. To fully appreciate our position, allow me to go back to basics by explaining what SASE is, then examine why Gartner has placed it in the Trough of Disillusionment category, and finally, showcase why our SASE solution delivers on the technology’s promises.















































Let's personalize your content