The Strategic Benefits of Randomized Decision-Making
Harvard Business Review
SEPTEMBER 26, 2023
In highly ambiguous and challenging contexts, a random approach to decision-making confers a number of advantages.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 articles random
articles random 
Harvard Business Review
SEPTEMBER 26, 2023
In highly ambiguous and challenging contexts, a random approach to decision-making confers a number of advantages.
The Crazy Programmer
JANUARY 18, 2022
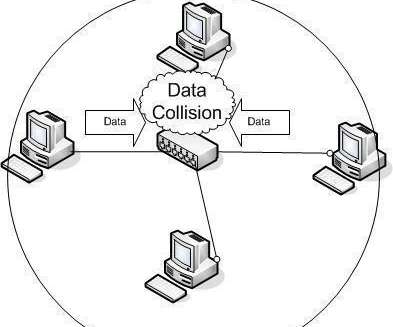
If yes, stay on this article because we have covered this topic in detail. And in this article, you will learn collision in computer networking and how it works. Please stay on this article and keep reading it step by step. And these stations will wait for a random time interval to start retransmitting the same signal.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Agile Engine
APRIL 25, 2024
This article will examine the principles that your competitors are likely leveraging to guide decision-making and boost conversions. By following behavioral science principles, designers can also encourage safer online behaviors — like choosing stronger passwords — or enable faster, more focused digital interactions.
The Crazy Programmer
MAY 9, 2021
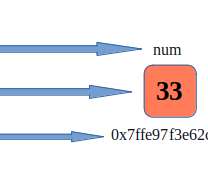
In this article, we will first look at how can we assign an address to a variable and then print the address using C language. some memory is allocated to the variable by the operating system which can be any random number but cannot be negative. First of all, we will take a look at how addresses are assigned to any variable.

The Citus Data
OCTOBER 26, 2023
This article was originally published on citusdata.com. It is recommended that you at least set up a pg_cron job to clean up after pg_cron: -- Delete old cron.job_run_details records of the current user every day at noon SELECT cron. schedule ( 'delete-job-run-details' , '0 12 * * *' , $$ DELETE FROM cron.

TechCrunch
FEBRUARY 24, 2022
In a 2022 Nature article , researchers used AI to fingerprint and re-identify more than half of the mobile phone records in a supposedly anonymous dataset. Instead of sharing data, companies would share data processing results combined with random noise. These failures led to differential privacy.
Perficient
JULY 2, 2023
Here in this article, we are going to see step-by-step code changes required to migrate docker-compose from v1 to v2. The above-mentioned “random$secretKeyString” was not working and was the root of the problem. The above-mentioned “random$secretKeyString” was not working and was the root of the problem.

The Daily WTF
JULY 27, 2021
The goal was to find the five most recent news articles and add them to the list. Now, this is a large scale CMS, so those articles need to be fetched from ElasticSearch. GetContentResult(); So, we search for all the news articles, excluding the deleted ones. This was their solution: [ JsonIgnore ] public List AllNews { get. {

The Daily WTF
NOVEMBER 22, 2023
So, it's a holiday in the US, and I'll be honest: the way I pick my holiday posts is by hitting the "Random Article" button until something fun pops out. That said, there were a few reasons that I wanted to rename the site, perhaps the biggest being that “Daily” and “What The F*” don’t quite describe it anymore.

O'Reilly Media - Ideas
JUNE 13, 2023
However, the citations I got were valid: real books and articles, with the authors listed correctly. A list of articles is certainly useful, but you still have to read them all to write the paper. More to the point, the article didn’t really make any connections to Rushdie’s fiction. That begged another question, though.
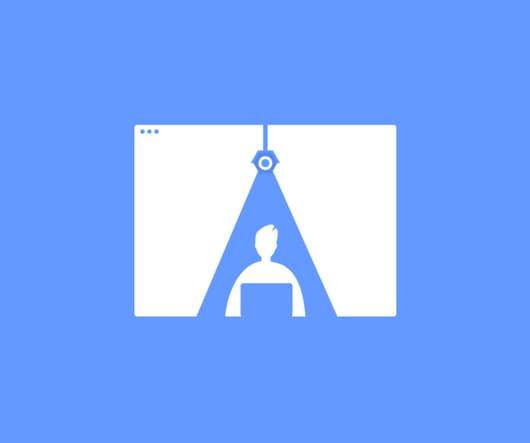
Hacker Earth Developers Blog
MARCH 2, 2022
Here is how HackerEarth does it: Random webcam snapshots: Randomized webcam snapshots are a great way to catch any type of malpractice attempt, like peering into another screen or verbal communication with someone in the room. Would you like to get monthly updates on our articles? Further Reading.
Perficient
MARCH 23, 2023
It is crazy how helpful and detailed it gets, and how many random questions it thinks to ask. P.S. Bing generated the featured image for this article. Ask me questions about the code and figure out why this might be happening. If you haven’t ever tried this, I highly recommend.

Apiumhub
OCTOBER 25, 2023
In this article, we explore the principles and techniques of prompt engineering, along with its limitations and potential applications. By following the principles and techniques outlined in this article, we can harness AI’s capabilities responsibly and achieve more accurate and contextually relevant results.

CIO
AUGUST 18, 2023
Natural language processing tokens help analyze unstructured data such as clinical notes and research articles. Prescription tokenization anonymizes drug names, dosages, and patient names. Image tokenization can de-identify medical images. Iron Mountain Bolstering Privacy Personal information is an integral part of medical records and data.

CIO
OCTOBER 24, 2023
For this article, we’ll focus on embedding models that work with text, although embedding models can also be used to organize information about other types of media, like images or songs. Ideally, that means you’re giving it accurate data, not just a random sampling of things it’s read on the internet.

CTOvision
OCTOBER 12, 2015
Random number generators, with seemingly high maximum throughputs and entropy often in practice only deliver the high entropy levels at very low throughputs. QuintessenceLabs quantum approach to generating random numbers addresses this challenge, offering rates of 1Gbit/sec, at 100% entropy. Related articles.
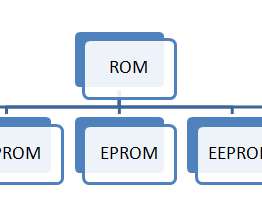
The Crazy Programmer
MARCH 30, 2021
The widely used type of primary storage is a volatile form of RAM or random access memory that means content present in RAM can be lost if power gets turned off. Share your thoughts about the article in the comment section below. It’s used in various other devices like printers, calculators, FAX machines, plotters, etc.

Toptal
NOVEMBER 14, 2017
Generative adversarial networks, among the most important machine learning breakthroughs of recent times, allow you to generate useful data from random noise. Instead of training one neural network with millions of data points, you let two neural networks contest with each other to figure things out.

The Daily WTF
JANUARY 3, 2022
One of its notable SEO tweaks was that it had a tag cloud that slapped a bunch of keywords together to give a sense of what kinds of articles had been posted recently. In fact, articles didn't get tagged at all. At least, that was the idea. So where was the tag cloud coming from? Popular tags. "> Popular tags. ">

The Daily WTF
APRIL 1, 2021
Also, for convenience, there's a dedicated TFT page which, long term, is probably a better tool than this article, since you'll be wanting to play with TFTs for a long time yet, I imagine. The TFT for the tft generator code is tft.js;dbbbf23d24502dba96913f18fa031203977b48db090a4a52ff6258a2c3bceecc

Perficient
DECEMBER 26, 2023
Though I’m keen to agree with the Big Think article that, instead, science-fiction inspires the people who shape the future. You can entirely suspend reality (even introducing randomness), and then come back and complete the full circle in a way that delights. Comedy removes our worries. Drama keeps us nervously intrigued.
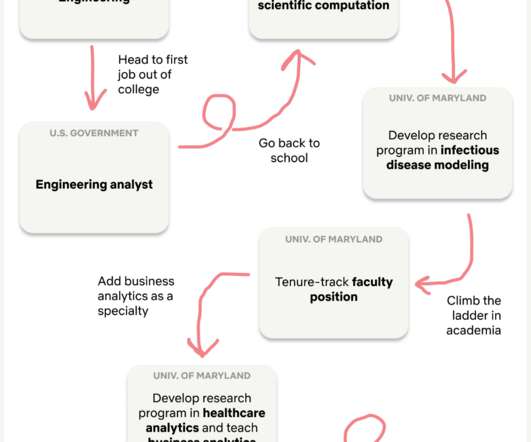
Netflix Tech
MAY 28, 2021
There is a mathematical concept called a random walk , which is essentially a path that is generated via a sequence of (seemingly) random steps. My (seemingly) random walk to Netflix looks a little something like this: Acknowledgment to Ritchie King for graphic design Why is my walk only seemingly random?
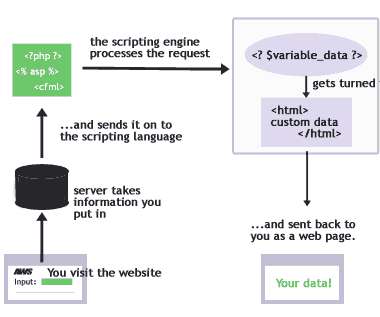
The Crazy Programmer
OCTOBER 15, 2021
In today’s article, we will understand the meaning and compare these two to understand some crucial differences. Then read this article and stay tuned with each element to get a deep understanding. The client-side scripting is more insecure than the server-side scripting because any random user can see its codes.

The Crazy Programmer
SEPTEMBER 22, 2022
You can also use this to analyze written comments made by your customers on your blog posts, news articles, social media, online forums, and other online review sites. You may use sentiment analysis to scan and analyze direct communications from emails, phone calls, chatbots, verbal conversations, and other communication channels.

High Scalability
JUNE 18, 2018
You can view the original article—H ow to implement consistent hashing efficiently —on Ably's blog. In this article, we’ll understand what consistent hashing is all about and why it is an essential tool in scalable distributed system architectures.
Netflix Tech
NOVEMBER 13, 2023
In this blog post, we will introduce speech and music detection as an enabling technology for a variety of audio applications in Film & TV, as well as introduce our speech and music activity detection (SMAD) system which we recently published as a journal article in EURASIP Journal on Audio, Speech, and Music Processing.

TechCrunch
MARCH 1, 2022
Full TechCrunch+ articles are only available to members. Since then, many of the key trends and themes we surfaced have come to pass: Airtable clinched an $11 billion valuation in December 2021 after raising a $735 million Series F with help from Salesforce Ventures and Michael Dell’s MSD Capital.
Dzone - DevOps
JULY 16, 2020
In this article, we outline how can small QA teams make the transition from manual to codeless testing to full-fledged automated testing. For example, a script to import test data into a database, a utility to generate random test data, etc. Do you or your team currently test manually and trying to break into test automation?

Apiumhub
JANUARY 31, 2023
In this article, we will go through how data leakage can occur, its consequences, and how industries, governmental institutions, and individuals may handle these concerns. Data Leakage As was already mentioned in the introduction, data leakage is an issue that can arise during the implementation of a machine-learning model.

The Impact of Kubernetes on the Enterprise
MAY 26, 2020
Whether predictable or random, scalability issues pose a major challenge for IT professionals. To read this article in full, please click here Various industries see seasonal spikes in demand—think tax filing or holiday shopping. More vexingly, an unlikely series of events could send a flood of requests that nobody anticipated.

CTOvision
JUNE 16, 2015
Here is more on how this new capability works: Most security applications today use “pseudo-random” numbers to generate keys. Pseudo-random numbers are not truly unpredictable and have been linked to multiple breaches, since they effectively reduce the strength of the encryption. Related articles.

O'Reilly Media - Data
DECEMBER 12, 2019
This article is meant to be a short, relatively technical primer on what model debugging is, what you should know about it, and the basics of how to debug models in practice. Random attacks: exposing models to high volumes of random input data and seeing how they react.

O'Reilly Media - Ideas
JUNE 24, 2020
But, since we’re thinking of them as random, the fact that Hong Kong has had a relatively minor outbreak that appears to have been controlled quickly means that several factors that limit spread were present, and added up. As attractive as it may be to think about complex systems, I’m not convinced that’s the best approach.

TechCrunch
MARCH 7, 2023
People are asking themselves if a link shared by a friend is actually legit and they’re wondering why they’re reading one article over the many others published on the same topic. I think these things are far more random than you think.” “It turns out that Artifact is actually very similar,” Systrom says.

The Citus Data
NOVEMBER 10, 2022
The change in PostgreSQL15 is that recovery now uses the maintenance_io_concurrency setting (default is 10, but you can increase it) to decide how many concurrent I/Os to try to initiate, rather than doing random read I/Os one at a time. The lowest hanging fruit is I/O stalls for large random workloads. posix_fadvise(10) ? ? ?
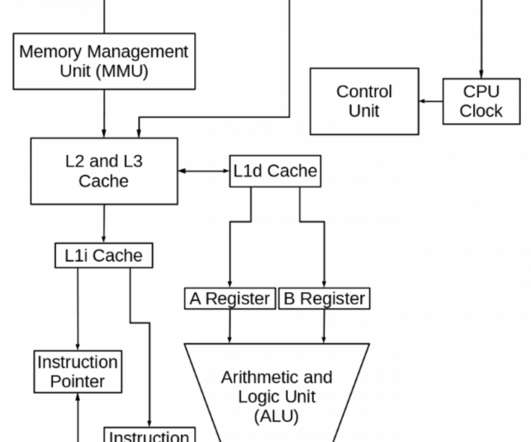
The Crazy Programmer
JUNE 4, 2021
In this article, we will take a look at the main 6 components of the Central Processing Unit, also known as the brain of the computer. Cache is a type of Random Access Memory which stores small amounts of data and instructions temporarily which can be reused as and when required. Data registers hold the memory operand.

Apiumhub
MARCH 2, 2023
As I explained in my previous article , GPT-3 (Generative Pretrained Transformer 3) is a state-of-the-art language processing model developed by OpenAI. In this article, we will provide a detailed guide on how to use the GPT-3 API, including how to set up your API key, generate responses, and access the generated text.

CTOvision
AUGUST 5, 2015
They use advanced engineering methods to generate “keys” that are truly random and therefore unhackable, as well as providing sophisticated key management solutions to enable pervasive and strong encryption. With this technology, a true random key is generated and shared. Related articles.

Erik Bernhardsson
MAY 27, 2015
The article describes a phenomenon unique to traffic where cars spread out when they go fast and get more compact when they go slow. You don’t know which one is which so you pick one at random. Saw this link on Hacker News the other day: The Highway Lane Next to Yours Isn’t Really Moving Any Faster. That’s supposedly the explanation.

Erik Bernhardsson
MAY 27, 2015
The article describes a phenomenon unique to traffic where cars spread out when they go fast and get more compact when they go slow. You don’t know which one is which so you pick one at random. Saw this link on Hacker News the other day: The Highway Lane Next to Yours Isn’t Really Moving Any Faster. That’s supposedly the explanation.

TechCrunch
APRIL 29, 2022
When I met with Lydia’s co-founders Cyril Chiche and Antoine Porte, they both had read my recent article on Zenly , another popular social app designed in Paris. This isn’t a random milestone. More importantly, the company is positioning its mobile app as a social product — not a fintech product. Image Credits: Lydia. Cyril Chiche.

Toptal
MARCH 23, 2017
In this article, Toptal Freelance Software Engineer Eugene Ossipov walks us through the basics of creating a Genetic Algorithm and gives us the knowledge to delve deeper into solving any problems using this approach.

Altexsoft
MAY 27, 2022
This article describes how data and machine learning help control the length of stay — for the benefit of patients and medical organizations. In collaboration, they trained random forests — ensemble algorithms consisting of many decision trees — to generate individual forecasts. Random Forest: LOS predictions for COVID-19 patients.

ProCal Tech
MAY 27, 2022
Transmission media and Signal corruption problem Home May 28, 2022 Telecommunications In this article from Procal, you will be learning about the transmission media and the problems faced due to signal degradation. As noted in the introduction to this article, modern communication systems use three main media: cable, radio, and optical.
Expert insights. Personalized for you.
Are you sure you want to cancel your subscriptions?

Let's personalize your content