Authentic Artists is building virtual, AI-powered musicians
TechCrunch
APRIL 7, 2021
Chris McGarry, who previously led music integration at Facebook’s Oculus, is taking a new approach to bringing music into the virtual world with his startup Authentic Artists. ” Authentic Artists is backed by investors including OVO Fund, James Murdoch’s Lupa Systems, Mixi Group and Mike Shinoda of Linkin Park.






































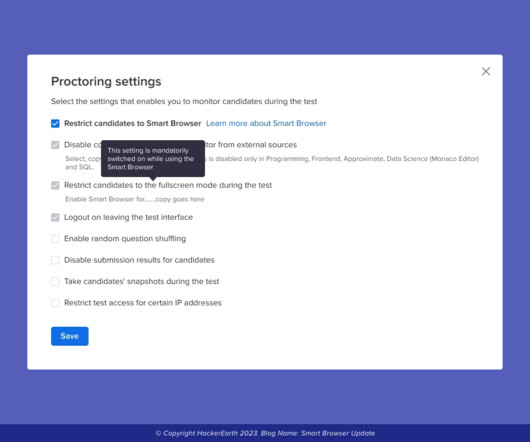













Let's personalize your content