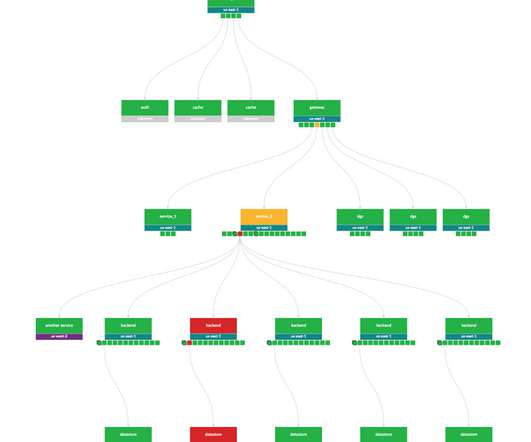
The GitHub Actions Worm: Compromising GitHub Repositories Through the Actions Dependency Tree
Prisma Clud
SEPTEMBER 14, 2023
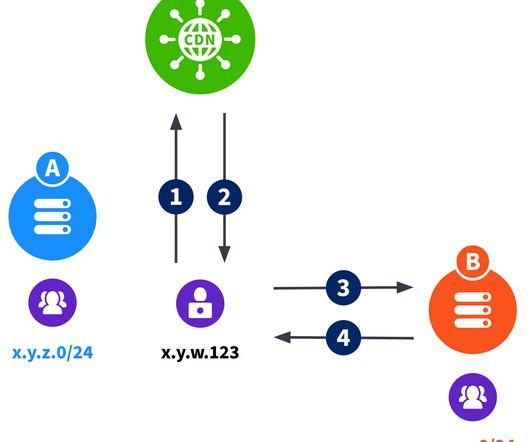
Get an in-depth look at the attack vectors, technical details and a real-world demo in this blog post highlighting our latest research. Note that this dependency action isn’t used as part of the action but only in the action’s workflow, a component process in the proper flow of the CI process. Reference a tag.














































Let's personalize your content