Prisma Cloud Achieves FedRAMP High Impact Level Status
Prisma Clud
MARCH 29, 2023
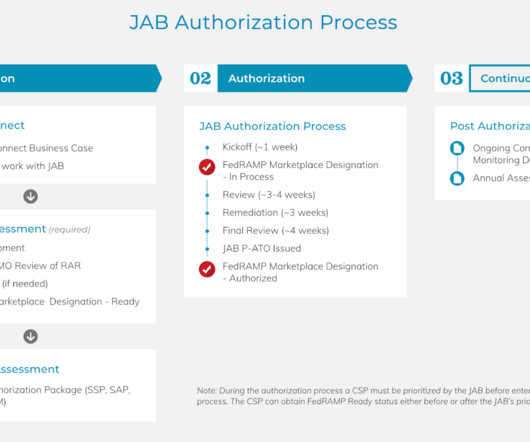
The FedRAMP Joint Advisory Board (JAB) has announced that Prisma Cloud has achieved FedRAMP High Impact Level Ready status. Palo Alto Networks expects Prisma Cloud to progress to High Impact Authority to Operate within the next 12 months. government agencies. Federal Government agencies.























Let's personalize your content