How Hacker News Crushed David Walsh Blog
David Walsh
OCTOBER 28, 2020
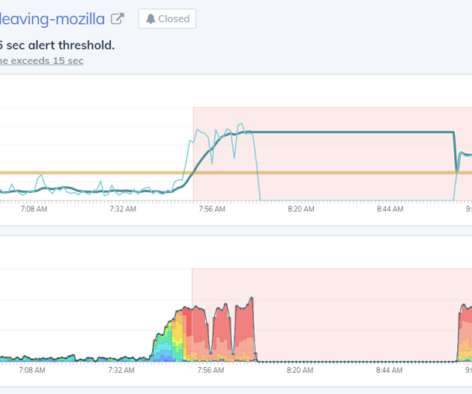
Traffic increased by 800% to his already-busy website, which slowed and eventually failed under the pressure. Request Metrics monitors performance and uptime for David’s blog , and our metrics tell an interesting story. This greatly limited the number of requests the blog was able to handle. Web Performance Lessons.
















































Let's personalize your content