The GitHub Actions Worm: Compromising GitHub Repositories Through the Actions Dependency Tree
Prisma Clud
SEPTEMBER 14, 2023
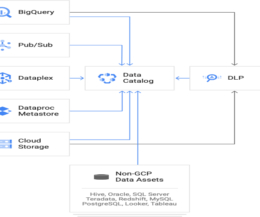
Get an in-depth look at the attack vectors, technical details and a real-world demo in this blog post highlighting our latest research. NPM Package Maintainer Email Hijacking Actions written in JavaScript usually involve dependencies maintained by developers who typically use email addresses to sign into NPM. Reference a tag.












































Let's personalize your content