Strengthening the Nessus Software Supply Chain with SLSA
Tenable
APRIL 16, 2024
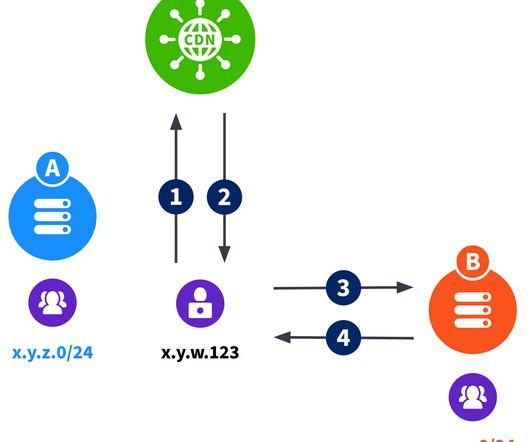
But sometimes we like to give you a peek behind the curtain to share how we protect our own house against cyberattacks – and that’s what this blog is about. Today we’re sharing our experience adopting the supply-chain security framework SLSA, with the hopes that the lessons we learned will be helpful to you.




































Let's personalize your content