Identifying & Deletion of Orphan Members in OneStream via simple Excel hacks
Perficient
MARCH 7, 2024
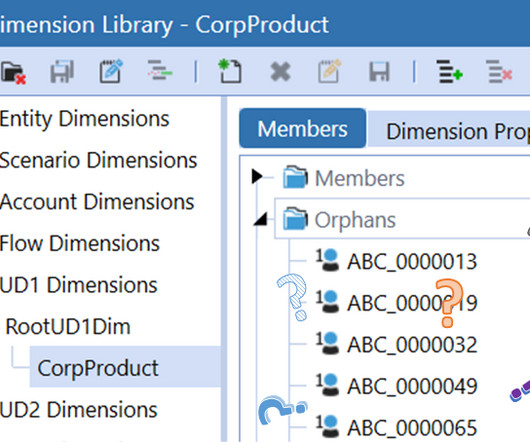
This blog focuses on simple Excel & Notepad++ based techniques, to populate the list of orphan members, and deleting them (if required). Tools Required Technique shared in the blog requires 2 software: Microsoft Excel Notepad++ Notepad++ is an open-source software available free of cost.






























Let's personalize your content