From Data Swamp to Data Lake: Data Catalog
Perficient
FEBRUARY 16, 2023
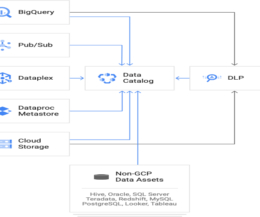
This is the second blog in a series that explains how organizations can prevent their Data Lake from becoming a Data Swamp, with insights and strategy from Perficient’s Senior Data Strategist and Solutions Architect, Dr. Chuck Brooks. Perficient Metadata Manager also provides data quality analysis and reporting capabilities.

















































Let's personalize your content