Radically simplify and expand Zero Trust to cloud workload
CIO
DECEMBER 21, 2023
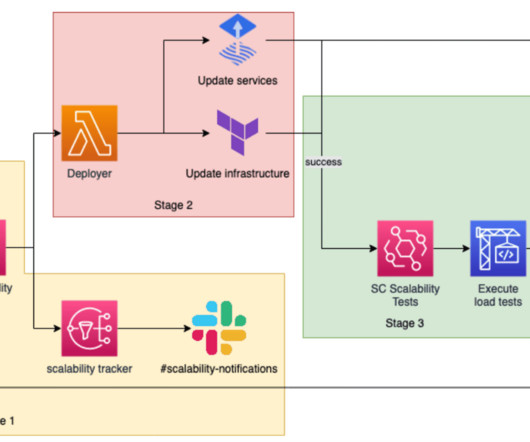
Zscaler’s innovative approach to securing workloads Zscaler recently announced significant advancements to the Zero Trust Exchange (ZTE) platform and Workload Communications to simplify cloud workload security.
















































Let's personalize your content