Radically simplify and expand Zero Trust to cloud workload
CIO
DECEMBER 21, 2023
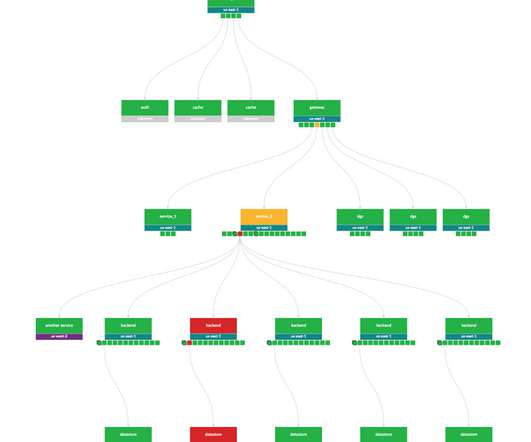
Backhauling to on-premises network security infrastructure for inspection and protection But relying on legacy security architectures amplifies lateral movement, increases operational complexity, and provides inconsistent threat and data protection.





































Let's personalize your content