Automated Deployment of CDP Private Cloud Clusters
Cloudera
JUNE 15, 2021
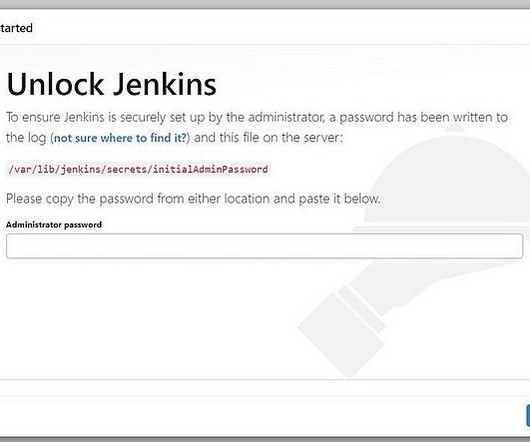
This blog will walk through how to deploy a Private Cloud Base cluster, with security, with a minimum of human interaction. Running the playbook. The overriding principle is that you should never need to amend the playbooks or the collections – everything that you wish to customise should be customisable through the definition.




















Let's personalize your content