What’s New in FlexDeploy 6.0
Flexagon
SEPTEMBER 22, 2022
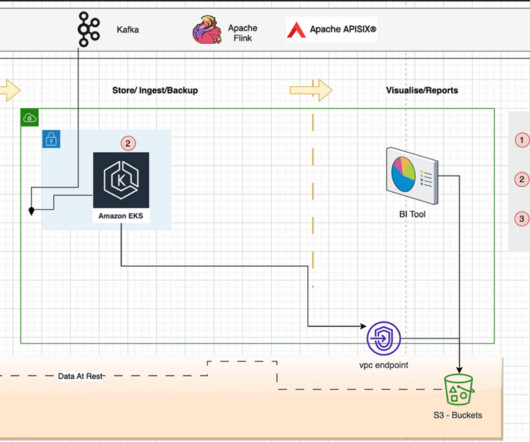
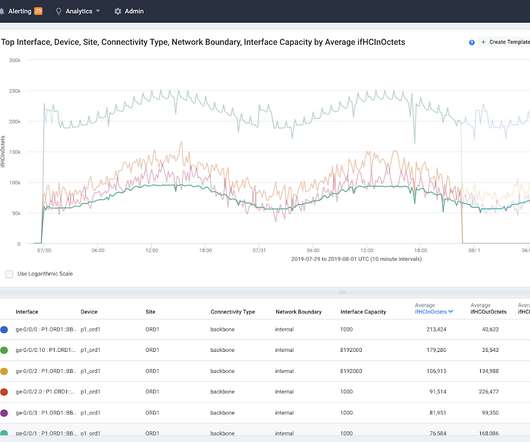
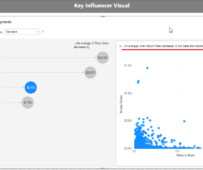
We have recently published a number of blogs on these new features, but you may be wondering what else is new and coming with FlexDeploy 6.0. Access recent, indicate favorites for quicker access, and tag several types of objects and search by tag. Assess quality metrics and thresholds and trigger actions based on results.








































Let's personalize your content