Radically simplify and expand Zero Trust to cloud workload
CIO
DECEMBER 21, 2023
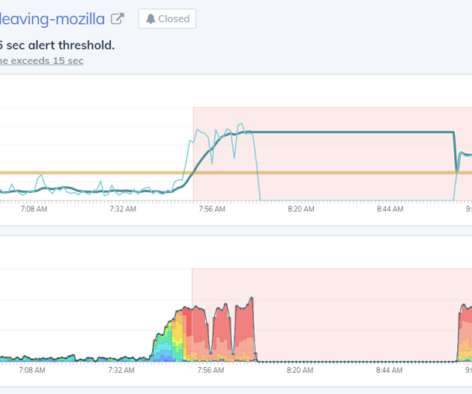
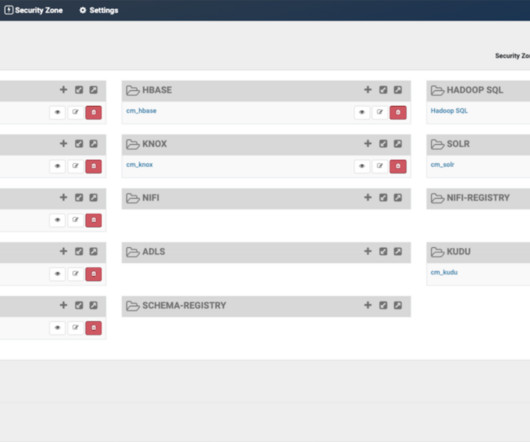
Workload segmentation using user-defined tags allows organizations to create custom security groups based on user-defined tags and native attributes on AWS. It helps to enforce granular threat and data protection policies per individual user session and maintain consistent security policies across all environments.















































Let's personalize your content