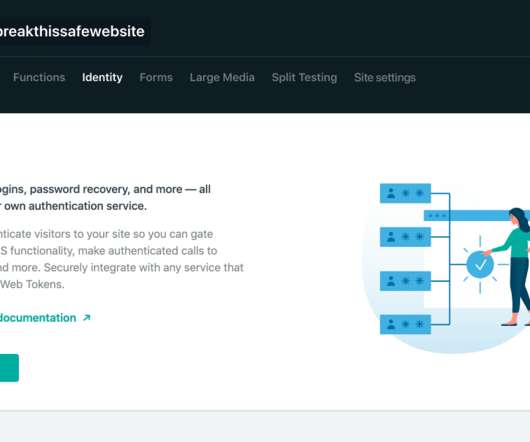
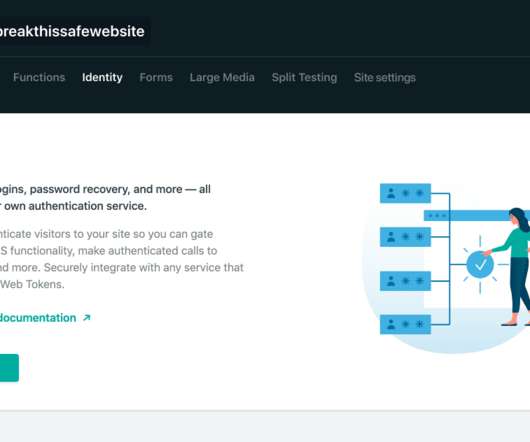
Manage and Authenticate Users with Netlify Identity
Netlify
DECEMBER 29, 2021
Keep an eye on the blog and on Twitter for each feature! “Authenticating users is a no-brainer”, said no one ever. I can’t wait to see (or not see if I’m not logged in) all the authentication functionality you create! login using external OAuth providers like GitHub, Google, GitLab, and Bitbucket.



























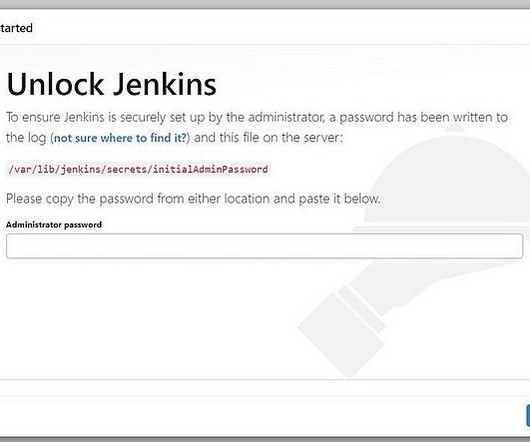























Let's personalize your content