How Hacker News Crushed David Walsh Blog
David Walsh
OCTOBER 28, 2020
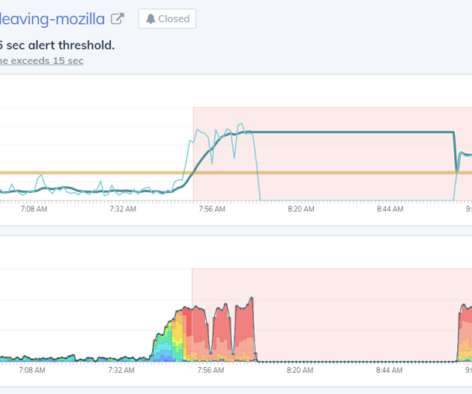
Request Metrics monitors performance and uptime for David’s blog , and our metrics tell an interesting story. Checking this endpoint in devtools, it returns an HTML snippet of what we would expect, the static sidebar content of David’s blog. This greatly limited the number of requests the blog was able to handle.














































Let's personalize your content