How to manage cloud exploitation at the edge
CIO
JULY 17, 2023
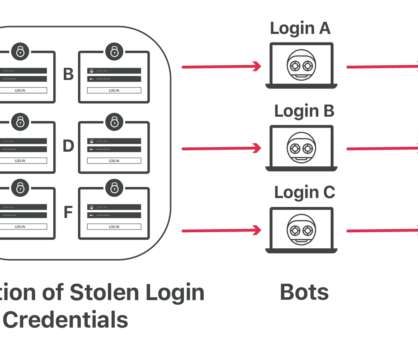
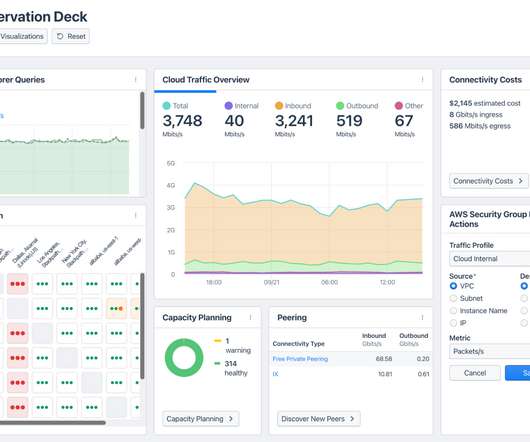
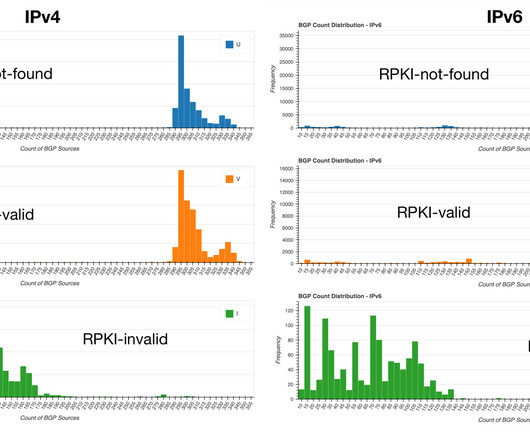
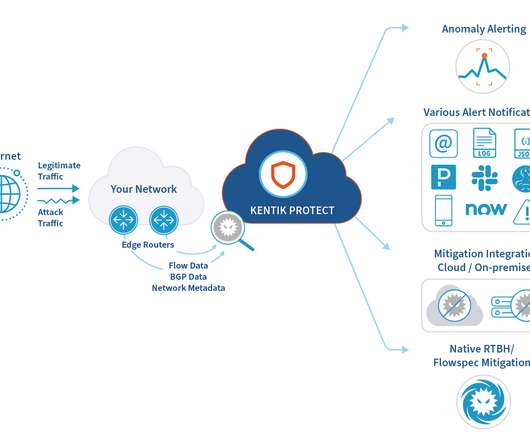
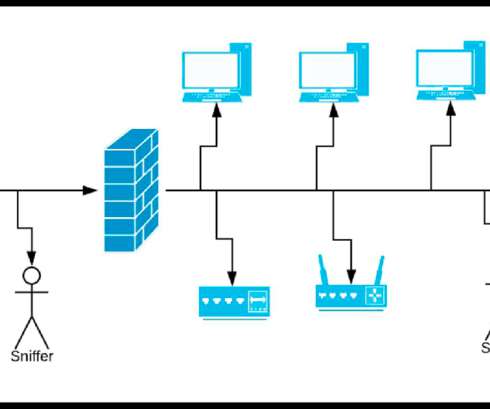
A cloud exploitation playbook could include attack vectors like distributed denial-of-service (DDoS) attacks, web application attacks, and bots – with the number one attack target being web applications. Respond to threats with speed Threat detection and mitigation speed are important for three key reasons. What can businesses do?














































Let's personalize your content