4 hybrid cloud obstacles to overcome this year
TechBeacon
FEBRUARY 27, 2020
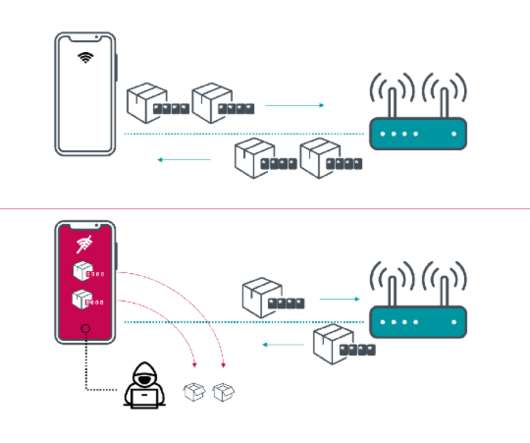
With both multicloud and hybrid cloud infrastructure approaches on the rise, many businesses—particularly those handling sensitive information, such as those in healthcare and finance—are pulling back from fully public cloud-borne operations in favor of a hybrid cloud approach.









































Let's personalize your content